Currently, Active Directory Server is often viewed as an outdated inconvenience in the cloud realm, yet there remains a significant demand for it, and we continue to receive various inquiries. Instead of just basic questions, we often encounter queries that lead us to wonder, “Did this function even exist?” As a result, there are many instances where past technical information is necessary for inquiries, making the review of legacy OS technical documentation quite essential.
There is a Microsoft community forum called Microsoft Q&A, where I noticed a thread related to on-premises issues. One post highlighted that even without utilizing roaming profiles, certificates can still be shared across devices, and users were experiencing issues with unexpected behaviors.
1. Sharing Desktop Environments Across Multiple Devices with Roaming Profiles
Roaming profiles are a feature that allows multiple devices to share user-specific information (profiles). Many people are aware that a profile folder exists for each user within the Windows Users folder. This mechanism creates a “copy” of certain data and files in the profile within an external shared folder and updates them during login and logout. Certificates are also included in the data contained in the roaming profile.
When discussing certificates, SSL (server) certificates are commonly recognized, but in this context, we are considering client (user) certificates and EFS (Encrypting File System) encryption certificates, which are used to verify client identity and encrypt files. For instance, if an EFS encryption certificate is shared, a file encrypted on device A can be decrypted and utilized on device B. Typically, files cannot be accessed on other devices unless they have been decrypted on device A beforehand (this is the purpose of this function).
2. What is Credential Roaming?
“Credential roaming” refers to the process where only certificate-related information (more specifically, the DPAPI usage area) is copied to the Active Directory user object, and this certificate is copied again to the profile when logging onto another device. It operates independently of the roaming profile functionality.
Why is such a feature necessary? According to Microsoft’s documentation, its original purpose is to “protect the credential area.” Windows user profiles are known to cause problems, so if a complicated issue arises, the solution may require “deleting and recreating” them. In such cases, the credential information, including certificates, would also be lost, necessitating measures to secure certificates for encrypted files. Uploading a backup to Active Directory serves this requirement.
The author also believes that a secondary purpose is to facilitate sharing among different versions of Windows. Windows emphasizes backward compatibility; however, significant changes have occurred in the OS architecture, particularly between Windows XP and Windows Vista. The user profile structure has evolved, making compatibility with previous versions unfeasible. When upgrading Windows, the (local) profile is converted internally and used as a new remote profile, which cannot be merged with the profile of the earlier version, thus preventing profile sharing between the two. Under such circumstances, it can serve as a means to “somehow” maintain compatibility.
3. Configuring Credential Roaming
As “credential roaming” pertains to user credentials, it is regulated by user group policies. [Group Policy Management] is the method accessed via the snap-in. Specifically, it is set up as follows:
- ・[User Configuration] – [Policies] – [Windows Settings] – [Security Settings] – [Public Key Policies] – [Certificate Services Client – Credential Roaming] Open [Enabled] Set
Regarding the above, Microsoft’s documentation suggests: [Default Domain Policy] It is advisable to set it there. If configured in this manner, it will affect all users (including Administrators!), making it preferable to create a new GPO directly linked to the domain for this setting. You can differentiate it by specifying particular users or groups in the security filter.
For detailed explanations on each setting item, please consult the Microsoft documentation (
- ※This is a URL to the web archive. Please access it at your own risk.
- ・Maximum tombstone credential lifetime (days): This option allows you to define how long roaming credentials for locally deleted certificates or keys will remain in AD DS.
- ・Maximum number of roaming credentials per user: This option lets you define the maximum number of certificates and keys usable with credential roaming.
- ・Maximum size of roaming credentials (bytes): This option places restrictions on credentials that exceed a specified size.
- ・Roaming stored usernames and passwords: This option enables you to include or exclude stored usernames and passwords from the credential roaming policy.
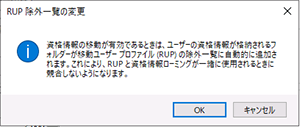
Upon attempting to set this up, a dialog box appears indicating the profile will be explicitly excluded from the Roaming User Profiles list. This implies that the settings will not overlap with the RUP settings.
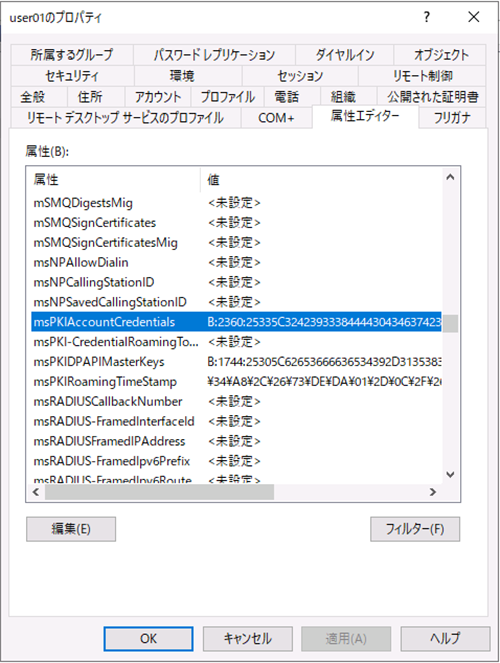
When I tested this, I successfully transferred the user certificate from device A to device B without issues. At that time, the following attribute values for the target user in Active Directory were established, confirming that the changes were reflected.
- ・msPKIAccountCredentials
- ・msPKIDPAPIMasterKeys
- ・msPKIRoamingTimeStamp
The timing of the change is as follows: If a certificate is deleted, this will also be reflected, so please note that it cannot serve as an archival backup.
- ・When a user logs on or off
- ・When locking/unlocking the desktop
- ・When the credentials are modified
I attempted to enable the “Rotation of stored usernames and passwords” option, but the contents of the Credential Manager varied by version—sometimes moved and sometimes not. The actual behavior observed was as follows:
- ・Windows XP SP3: Not moved
- ・Windows Vista SP2: Moved
- ・Windows 10 22H2: Not moved
- ・Windows Server 2019: Not moved
I found it necessary to refer back to the Microsoft documentation (Certs On Wheels: Understanding Credential Roaming – Microsoft Community Hub) and upon reviewing it again, I noted that “Credential roaming only supports x.509 v3 certificates and RSA or DSA key pairs stored in the user’s credential store.” I suspect that a different encryption algorithm may be employed in more recent Windows versions, which does not meet these requirements, thus preventing the transfer (though I have not confirmed this).
According to Microsoft documentation, this option is not enabled on Windows XP because it was first implemented in Vista and later versions.
To disable this, you can either disable the policy or revert it to “not configured,” but the aforementioned attribute will remain on the user object. Unfortunately, this cannot be deleted through the GUI and requires using a command. First, employ ldifde.exe, which was recommended by Microsoft back then.
- ※This is a URL to the web archive. Please access it at your own risk.
- 1.Identify the username you wish to delete in advance (user01 in this case).
- 2.Execute ldifde.exe -f dimsdelete.ldf -r “(cn=user01)” -l dn
- 3.Open the exported dimsdelete.ldf using Notepad.
- 4.Modify the content as follows:
dn: → Do not alter
Change changetype: to modify
delete: → Add as shown in the screenshot, remembering the “-” (separator).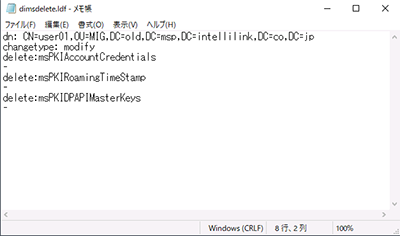
- 5.Run ldifde.exe -i -f dimsdelete.ldf
- 6.Use ldifde.exe -f dimsverify.ldf -r “(cn=user01)” -l msPKIAccountCredentials, msPKIRoamingTimeStamp, msPKIDPAPIMasterKeys to extract this attribute value.
- 7.Upon opening the exported dimsdelete.ldf in Notepad, you will observe that the attribute value no longer exists.
Alternatively, you can utilize the PowerShell Set-ADUser cmdlet to clear the attribute by specifying the -Clear option.
Get-ADUser -filter * -properties * | Where-Object {$_.msPKIAccountCredentials -and $_.msPKIDPAPIMasterKeys -and $_.msPKIRoamingTimeStamp} | Set-ADUser -Clear msPKIAccountCredentials, msPKIDPAPIMasterKeys, msPKIRoamingTimeStamp
This script extracts user objects that have values for all three target attributes and sets those attributes to “not set.” Note that unless you include the three attributes in the -properties option of Get-ADUser (as this script includes all attributes), extraction and operation may not be feasible.
Despite that, Active Directory PowerShell is immensely powerful. With Active Directory gaining attention in Windows Server 2025, many individuals will likely be enhancing their skills for the first time. While its usefulness is uncertain, I look forward to periodically sharing more information on it.
Understanding Active Directory: Credential Roaming and Roaming Profiles
In today’s rapidly evolving cloud landscape, Active Directory Server is often viewed as a relic. However, the demand for knowledge about its features remains high, especially when inquiries delve into functionalities that many may have overlooked. A significant point of interest has emerged regarding roaming profiles and credential roaming, particularly in how they pertain to user certificates and security management within Active Directory.
1. Sharing Desktop Environments on Multiple Devices Using Roaming Profiles
Roaming profiles offer a mechanism for sharing user-specific settings and data across multiple devices. Each user has a dedicated profile folder located in the Windows Users folder. Roaming profiles work by storing a copy of certain user data in a shared folder, which gets updated upon logging in and out. This feature enables seamless access to user-specific settings, including certificates.
While SSL certificates are commonly discussed, client certificates and EFS (Encrypting File System) certificates are crucial in managing user identity and securing files. For instance, if a user has an EFS encryption certificate, the files encrypted on one device (Device A) can be accessed on another (Device B) without needing to decrypt them on Device A first. This capability exemplifies the utility of roaming profiles in maintaining a cohesive user experience across different devices.
2. What is Credential Roaming?
Credential roaming is a distinct feature whereby only the essential certificate-related data (specifically, the DPAPI – Data Protection Application Programming Interface usage area) is duplicated into the Active Directory user object. This ensures that when a user logs onto a different terminal, the relevant credentials are made available to the new profile independently of roaming profiles.
The importance of credential roaming becomes clear when considering its necessity in a dynamic user environment. Often, user profiles may face complications requiring deletion and recreation. In such cases, preserving the credentials is vital, and utilizing Active Directory as a backup method meets this requirement.
Additionally, credential roaming supports compatibility between different Windows versions. Given the structural changes in user profiles from Windows XP to Vista and beyond, credential roaming provides a workaround for maintaining access to essential certificate data, even when direct profile sharing is not feasible.
3. Configuring Credential Roaming
Credential roaming is governed by user group policies, and the configuration process can be executed via the Group Policy Management Console. Below is the method for setting up credential roaming:
- ・Navigate to [User Configuration] – [Policies] – [Windows Settings] – [Security Settings] – [Public Key Policies] – [Certificate Services Client – Credential Roaming]. Open and set to [Enabled].
It is advisable to implement these settings within the [Default Domain Policy], but creating a new Group Policy Object (GPO) linked directly under the domain is typically more effective. By doing so, you can manage which users or groups have access to this policy through security filtering.
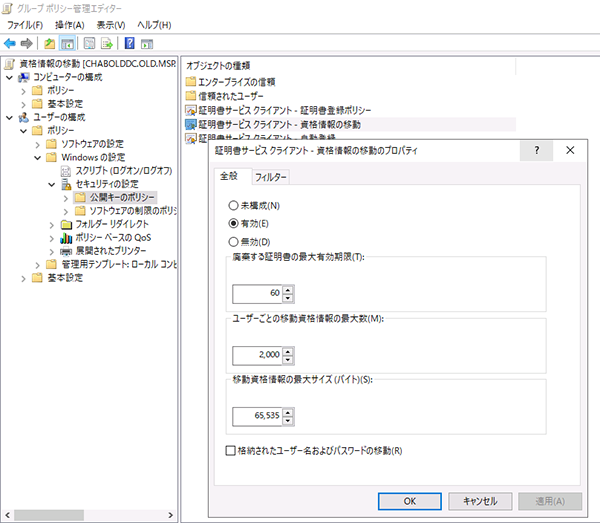
Key Configuration Options
- ・Maximum tombstone credential lifetime (days): Define how long roaming credentials for deleted certificates remain in AD DS.
- ・Maximum number of roaming credentials per user: Determine the upper limit of credentials a user can possess.
- ・Maximum size of roaming credentials (bytes): Restrict credentials exceeding a specified size from roaming.
- ・Roaming stored user names and passwords: Specify whether stored user names and passwords are included or excluded in the roaming policy.
If you configure these settings, you may receive a dialog indicating that the profile will be excluded from the Roaming User Profiles list, highlighting the independence of these functionalities.

Benefits of Credential Roaming
Implementing credential roaming enhances user experience and security in several ways:
- **Seamless User Experience:** Users can log into different devices without losing access to their certificates, promoting productivity.
- **Enhanced Security:** Regular backups of sensitive credentials in Active Directory mitigate the risk of data loss due to profile issues.
- **Support for Compliance:** For organizations that need to adhere to data protection standards, credential roaming helps maintain up-to-date access to encrypted materials.
4. First-Hand Experiences and Case Studies
In a real-world scenario, a mid-sized firm adopted credential roaming to address the challenges faced by their sales team, who frequently switched devices for client meetings. By implementing credential roaming, they ensured that crucial encryption certificates were accessible on multiple devices without cumbersome manual transfers. Feedback from the team highlighted an improvement in efficiency and a significant reduction in frustration related to accessibility issues.
Common Pitfalls and Practical Tips
When configuring credential roaming, there are several common issues that may arise, along with helpful practices to avoid them:
- 1.**Compatibility Considerations:** Ensure that all devices meet the minimum requirements for credential roaming, particularly regarding OS versions. Check Microsoft documentation for details on supported configurations.
- 2.**Monitoring and Maintenance:** Regularly review the policy settings to ensure they align with organizational changes, preventing any potential security lapses.
- 3.**User Training:** Provide users with adequate training regarding how credential roaming works and its impact on their profiles to minimize misuse or misunderstanding.
5. Troubleshooting Credential Roaming Issues
If issues arise with credential roaming, administrators can take the following steps:
- 1.Check Group Policy Object (GPO) settings to ensure configurations are correctly applied.
- 2.Utilize logging and monitoring tools to review errors related to credential transfers between devices.
- 3.Refer to community forums or Microsoft’s support documentation for fixes reported by other users facing similar challenges.
6. Conclusion
Active Directory, despite being labeled as outdated, still plays a crucial role in the management of user credentials and profiles in a cloud-centric world. A deep understanding of features like credential roaming and roaming profiles empowers organizations to harness the full potential of their infrastructure while ensuring security and efficiency.
