Today we will see together how to configure a VPN server on the UDM Pro or UDM Pro SE. For some time now, the UDM Pro SE has offered two options for setting up a VPN, either the traditional and well-known L2TP/IPSEC VPN, or WireGuard. This is the first solution I’m going to present to you today, however, I’ll be back shortly with another article regarding setting up a VPN with WireGuard.
The VPN (Virtual Private Network) is a way to connect your devices (computers, tablets, smartphones, etc.) remotely to your network using a secure and private connection. This will allow you to access your Windows servers, NAS servers or even your printing devices from the outside in complete safety. One of the most widely used VPN protocols is L2TP/IPSEC, which offers a combination of security and ease of use. L2TP (Layer 2 Tunneling Protocol) was created by a collaboration between Microsoft and Cisco Systems in 1999.
Configuration VPN L2TP/IPSEC sur Unifi
Attention, in my case, the UDM Pro being behind a Livebox, it is configured in DMZ. that is to say that all the ports are open to the UDM Pro, it is then this one which will act as firewall and router. Depending on your configuration (if you are in bridge for example), the procedure may differ slightly. What you have to keep in mind is that the L2TP/IPsec protocol uses UDP ports 500 and 4500. It is therefore necessary that they are open.
On the UDM side, this will be done automatically, on your box side, it depends on your configuration. In Bridge, no port to open, if like me you are in DMZ, no port to open either, if your UDM is not in DMZ, then you will have to open these ports and redirect them to your UDM in order to do dual-NAT.
If it’s not clear, feel free to use the comments. We will now move on to setting up the VPN.
VPN configuration on UDM (Pro and SE)
From the Network application of your UDM Pro / SE, click on ” Settings » then in the section « Teleport & VPN ” click on ” Create New ” in front of ” VPN Server« .
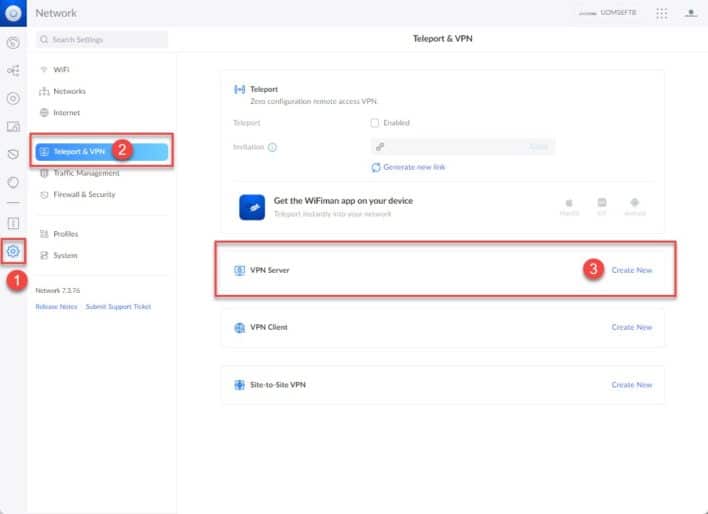
Here, if you have a UDMPRO in “SE” version, select L2TP, we will see in a future article the configuration with WireGuard. Add a name to your VPN network.
You can retrieve the pre-shared key or create your own, finally, in the ” Server Address » , it is the WAN IP which must appear, unless like me you are in DMZ, then it will be the IP of your UDM on the network of your Box.
This is where you will also be able to create your users, to do this click on ” Create New User » .
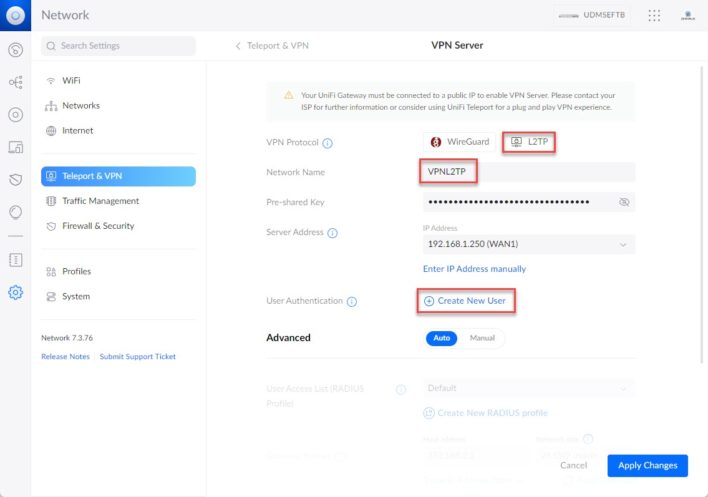
Create your users here to grant them the right to connect to the VPN. Click on ” Create User ” to validate.
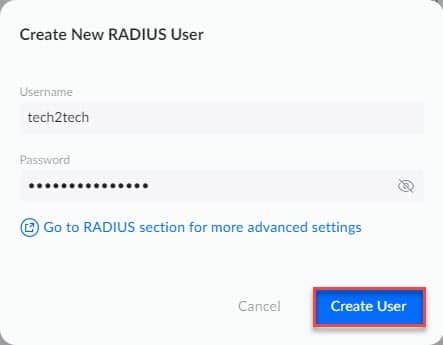
You will then be able to use this VPN as it is, or go a little further in the configuration by selecting “Manual” in the “Advanced” section.
In particular, you will be able to change the network used by the VPN, add your DNS or even activate strong authentication for the use of the MS-Chapv2 protocol for Windows.
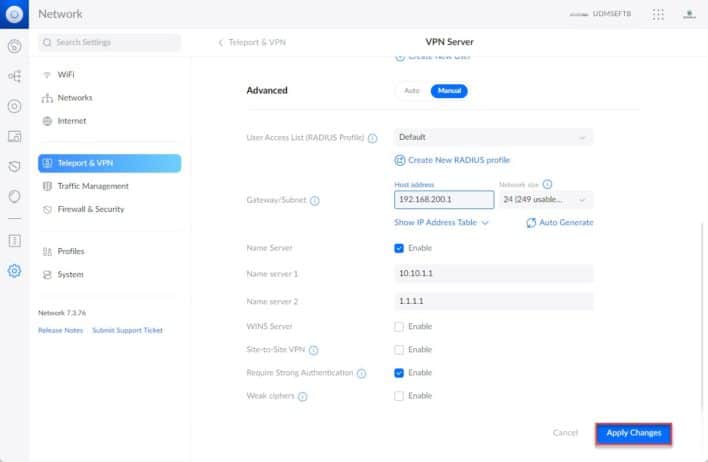
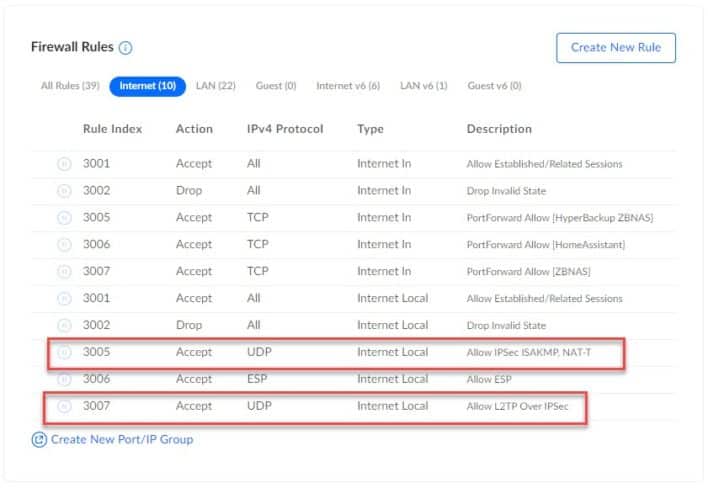
Firewall rules are automatically created on UDM once the VPN is created.
Connexion au VPN Unifi UDM via Windows
Now that our VPN is installed and configured, we will see how to connect to the VPN from outside with Windows. Remember to do your tests from outside your network (with connection sharing for example). The protocol advantage L2TP/IPSEC is that we will not need to install any application, it is integrated into Windows.
Here is the method on Windows 11 (it remains very similar to Windows 10)
- From the Windows settings, click on ” Network and Internet » then select VPN
- Click on Add a VPN
- Here select Windows (embedded) as a VPN provider, add a custom name for your VPN, your UDM’s WAN ip or its custom DNS.
Select L2TP/IPsec with pre-shared key then enter the pre-shared key that you had configured in the UDM VPN. - Finish by adding your username and associated password. Click “Save to Finish”.
- We must now activate MS Chap v2 on our virtual network card.
- Right-click on the start menu and select “Run” (or use the shortcut “Win+R”)
- Launch the command ncpa.cpl which will allow you to directly access all of your network cards.
- Access the properties of the virtual network card dedicated to your VPN
- In the security tab, click on “Allow these protocols” then select “MS-CHAP v2”, validate by clicking on “OK”.
We’re almost done. If you have your UDM in bridge, then your VPN should already be functional. However if like me it is behind NAT (DMZ or Double NAT), it is necessary to add a registry key so that it is functional. (More info here)
For UDMs in NAT
As explained above, if you want to use Windows as a VPN client and your UDM is in NAT, then you will have to make a small modification in the registry. Here’s how :
- On your Windows computer, use the “Win + R” shortcut to be able to run the “Regedit” command.
- From the registry, find and select it under the following registry key:
HKEY_LOCAL_MACHINESYSTEMCurrentControlSetServicesPolicyAgent - Add a DWORD value (32 bit) bearing the name AssumeUDPEncapsulationContextOnSendRule
- Give the value “2”
- Restart the computer (essential).
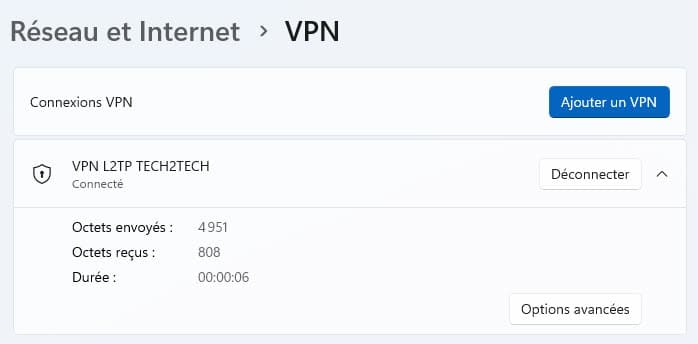
Now that our machine is configured correctly, we will be able to launch the VPN connection. To do this, either directly from the settings in the “Networks” option.
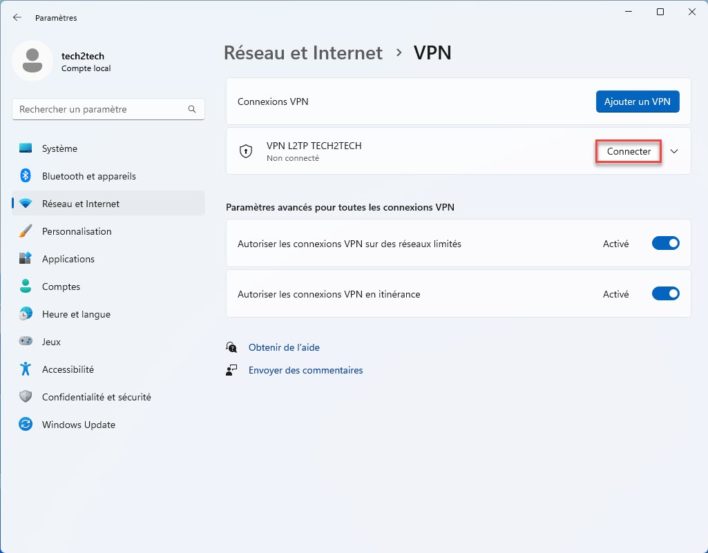
Either directly from quick actions, you should now see your VPN. Just click on ” Connect » !
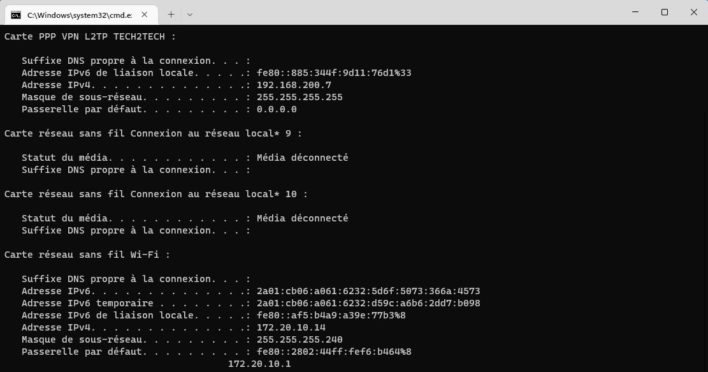
A simple ipconfig will then allow you to check that you have correctly recovered the IP address of your VPN tunnel.
That’s it, you should now be able to easily create a VPN connection from your Ubiquiti UDM. L2TP being a recognized protocol, it is available on any type of device, so it will be possible to mount your VPN also on Linux, macOS or even your smartphone.
Be careful, by default once connected to your VPN, you have full access to all of your network and your VLANs. If you need to block access to certain IP addresses or VLANs, you will need to create new “LAN OUT” firewall rules. I talk regarding it in my video, feel free to take a look if you want to deepen the subject.
We will come back soon with an article to explain how to set up a site-to-site VPN, but also a VPN via WireGuard.


