Microsoft’s action once morest unreliable Office macros comes with good news and bad news. The good news is that the use of Office macros in email attachments or links has been reduced. The bad news is that attackers are changing tack and stepping up their use of Windows .LNK shortcut links.
According to security firm Proofpointsince Microsoft clamped down on Office macros, attackers use container files such as ISO, RAR attachments, and Windows Shortcut (LNK) files.
A turning point
A turning point in the use of macros came in February, when Microsoft announced that it would implement a default blocking of Visual Basics for Applications (VBA) macros coming from the internet starting in april. This deployment plan was delayed until this week.
“The most notable change is the emergence of LNK files; at least 10 tracked malicious actors started using LNK files since February 2022. The number of campaigns containing LNK files has increased by 1675% since October 2021,” note Proofpoint.
According to Proofpoint, the number of email attachments containing malicious macros decreased by approximately 66% between October 2021 and June 2022.
Block macros
Adoption of .LNK files by malicious actors took place before February, as Microsoft’s macro blocking measures began years ago.
The malicious use of Office Macros – a script in Word or Excel files that automates repetitive tasks – is a handy technique for attackers. Indeed, the flaw cannot be fixed, and the tactic is to encourage employees to activate a function that most do not need.
Microsoft’s latest measure, implemented this week, is to make Office apps, by default, block VBA macros in any attachments or links in received emails. This eliminates the need for administrators to configure domains to block untrusted VBA macros and makes it more difficult for users to enable macros through the back door.
Since 2016, Microsoft has gradually imposed more restrictions on the execution of macros. At the time, the company claimed that 98% of threats targeting Office used macros. In January, Microsoft also disabled Excel 4.0 (XLM) macros by default. XLM has been added to Excel in 1992but is still in use, although VBA supplanted it in 1993.
Hey, LNK, watch out !
In 2018, Microsoft gave antivirus vendors a way to integrate with Office to inspect files for malicious VBA macros. She added the XLM macros to this antivirus interface in March because attackers had started using XLM
“Although more rudimentary than VBA, XLM is powerful enough to provide interoperability with the operating system, and many organizations and users continue to use its functionality for legitimate purposes.” Cybercriminals know this, and they are increasingly abusing XLM macros to call Win32 APIs and execute shell commands.
XLM, also known as XL4, has been adopted by the cybercriminal groups behind the Emotet malware. Again, the use of XLM correlates with Microsoft’s decision to block these macros and let antivirus vendors inspect Office files for these scripts.
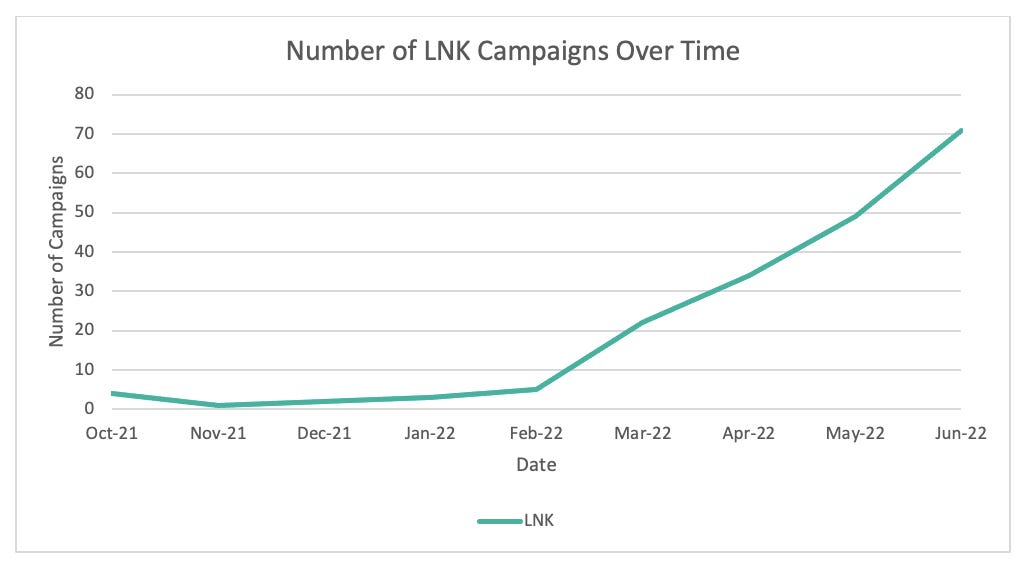
Image : Proofpoint.
“Usage of the XL4 macro peaked in March 2022. This is likely due to the fact that TA542, the actor spreading the Emotet malware, ran more campaigns with higher message volumes than in previous months. . In general, TA542 uses Microsoft Excel or Word documents containing VBA or XL4 macros. Emotet’s activity then declined in April and it began using other delivery methods including Excel Add In (XLL) files and LNK zipped attachments in subsequent campaigns,” Proofpoint notes.
Source : ZDNet.com



