With iOS 16.3 and macOS 13.2, Apple will enable end-to-end encryption of virtually all data stored in the cloud, globally. The United States is entitled to it since iOS 16.2 delivered late last year. The release candidate of iOS 16.3 contains the function and makes it possible to use it now.
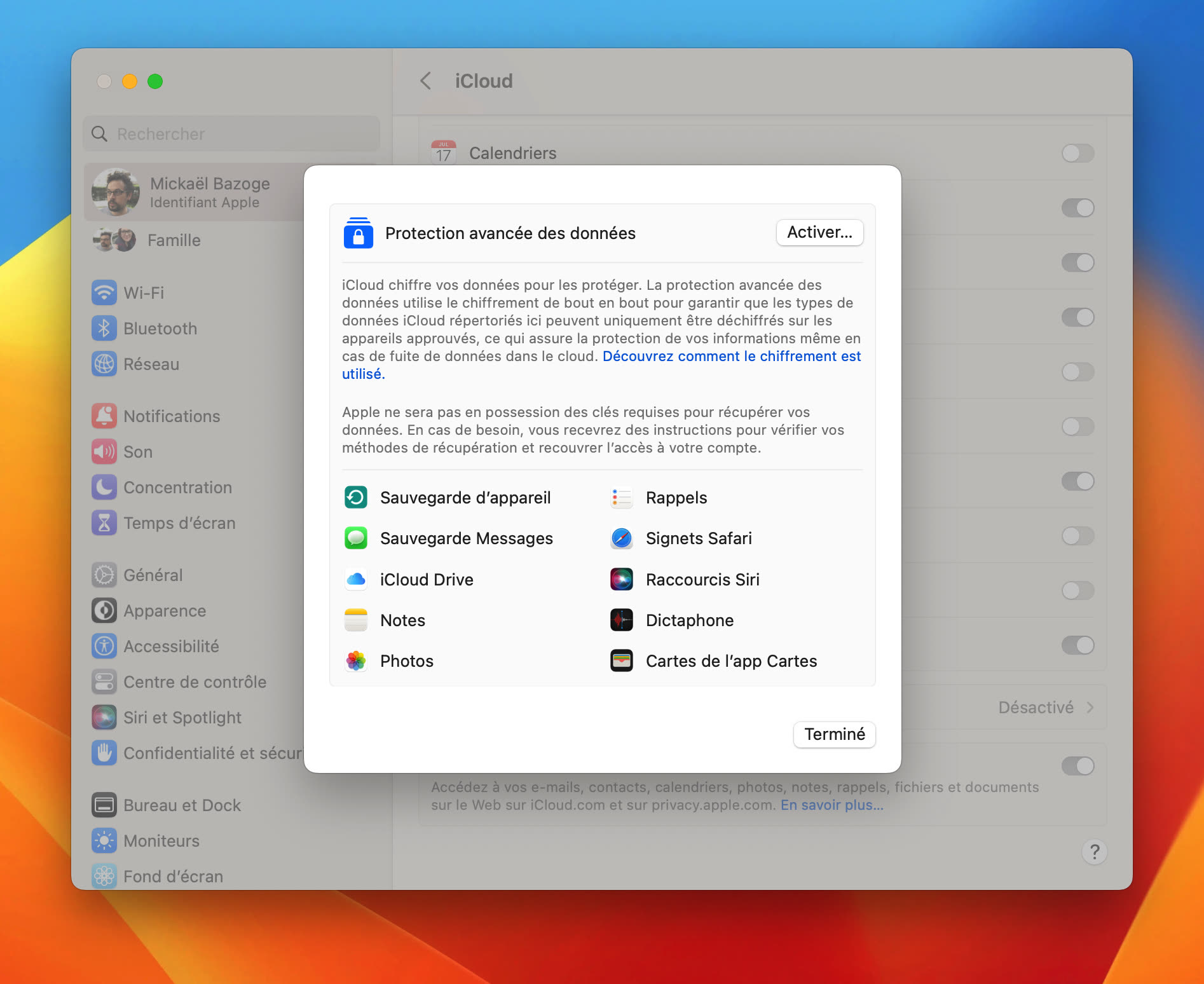
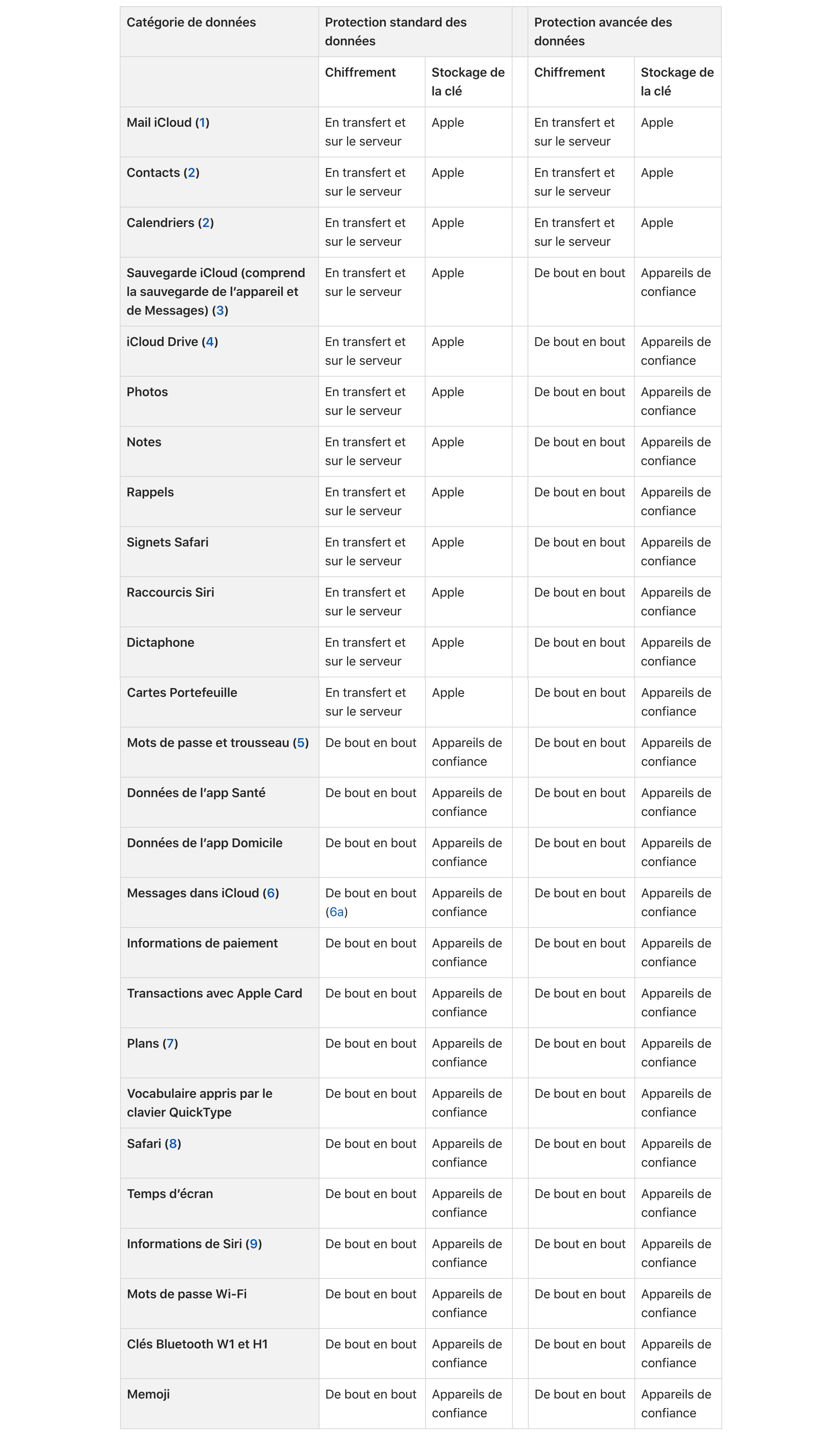
This function of advanced data protection will encrypt 23 categories of data (compared to 14 for the default basic function), including photos, notes and especially the iCloud backup that Apple will therefore no longer be able to unlock – this was useful when the security forces the order were asking for information regarding a suspect. Without a decryption key, the manufacturer will therefore be unable to share the data contained in the backup.
iCloud email, contacts and calendar will be the last major categories of data not to be end-to-end encrypted on Apple’s servers. This is data that works in conjunction with standard protocols and systems.
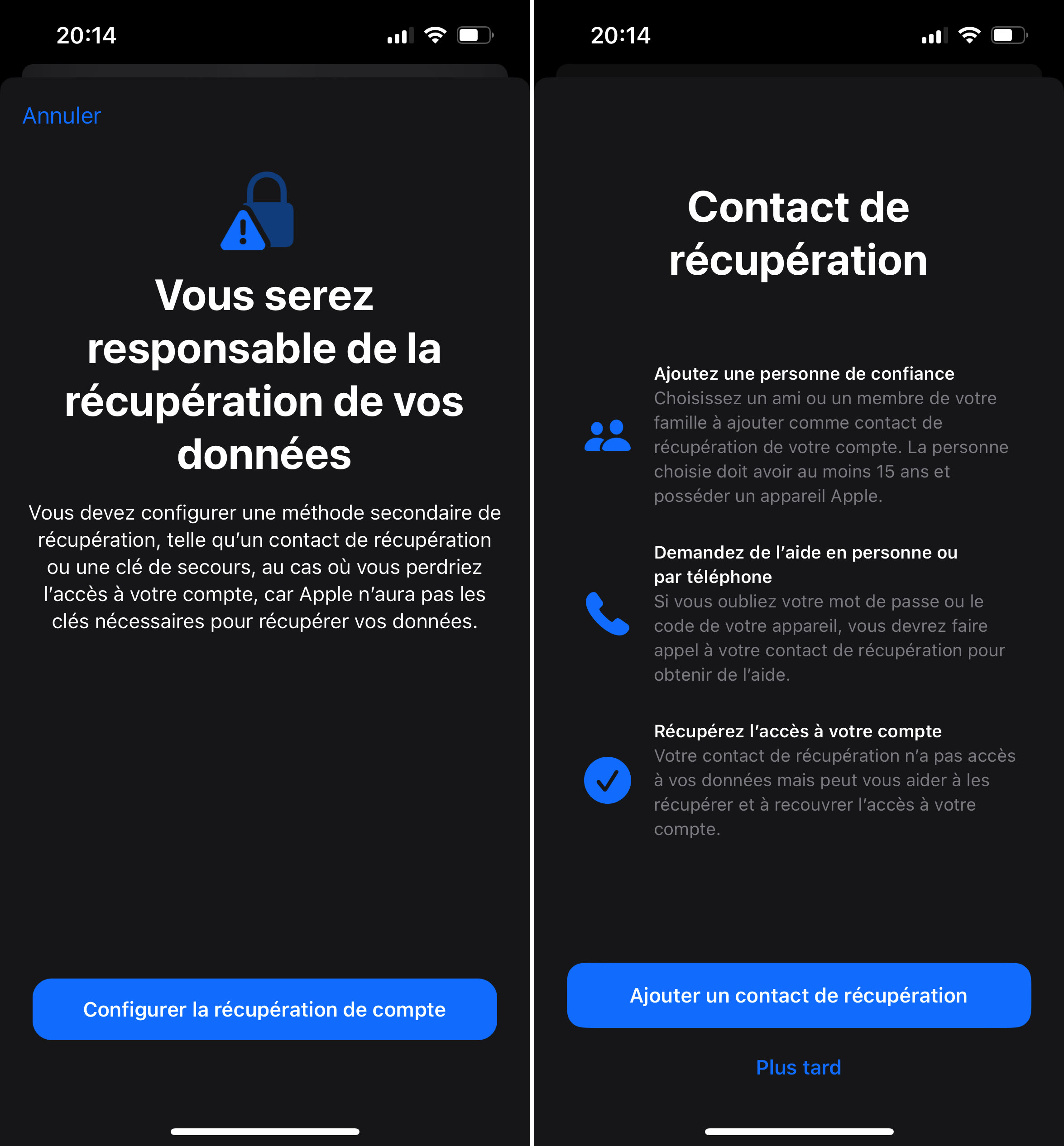
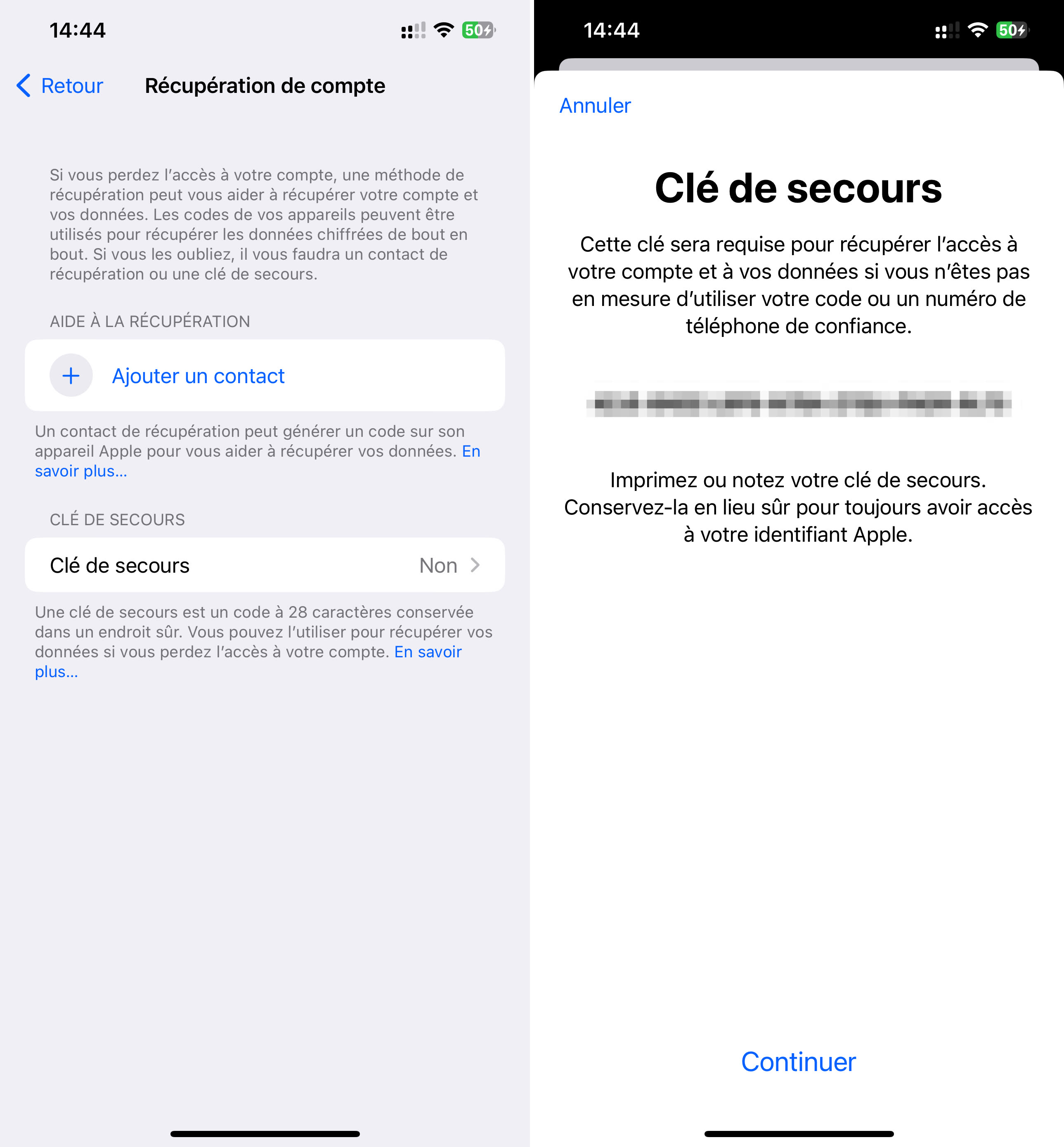
This enhanced protection does not come without responsibility for the user. iOS also specifies it in black and white, explaining that it is necessary to configure a secondary method of recovery, such as a contact or a spare key. A key that must not be lost: if this is the case, Apple will not be able to help you recover the data.
Do you need this enhanced protection? For Apple, hardening user data security in the cloud becomes more urgent than ever “, highlighting the number of intrusions which tripled between 2013 and 2021, exposing 1.1 billion personal data last year. However, the manufacturer directs it more to users who need a higher level of security, political personnel, journalists, human rights activists, etc.
Good to know: it is possible to return to standard protection at any time. The device will then retrieve the required encryption keys.
Craig Federighi: End-to-end encryption of all iCloud will be the responsibility of the user
This safety function is in addition to the one that allows use 2FA security keys to securely log in to your Apple account, it is available in iOS 16.3.
Verification of ignition keys in iMessage is also expected shortly. It displays alerts in the event that an exceptionally sophisticated threat (a state-sponsored attack, for example) manages to reach the cloud servers and implant bugging devices to access these encrypted communications. Users can also compare contact verification codes on FaceTime themselves.




