You would agree that the main function of an operating system is to provide a safe execution environment where different applications can run safely. This necessitates the requirement of a basic framework for uniform program execution in order to utilize hardware and access system resources in a secure manner. The Windows kernel provides this basic service in all but the most simplistic operating systems. To enable these fundamental features for the operating system, several parts of the operating system initialize and run at system startup.
In addition to this, there are other features capable of offering initial protection. These include:
- Windows Defender – It offers complete protection of your system, files and online activities from malware and other threats. The tool uses signatures to detect and quarantine applications known to be malicious in nature.
- Filtre SmartScreen – It always warns users before allowing them to run any untrusted application. Here it is important to keep in mind that these features are only able to offer protection following Windows 10 has started. Most modern malware, and bootkits in particular, can run even before Windows startup, thus hiding and completely bypassing the security of the operating system.
Fortunately, Windows 10 offers protection even at startup. How? Well, for that, we first need to understand what rootkits are and how they work. Later, we will be able to deepen the subject and discover how the protection system of Windows 10 works.
archyde news
Rootkits
Rootkits are a set of tools used to hack a device by a cracker. The cracker attempts to install a rootkit on a computer, first gaining user-level access, either by exploiting a known vulnerability or cracking a password, and then recovering the required information. It conceals the fact that an operating system has been compromised by replacing vital executables.
Different types of rootkits run during different phases of the boot process. These included,
- Kernel rootkits – Developed as device drivers or loadable modules, this kit is capable of replacing part of the operating system kernel so that the rootkit can start automatically when loading the operating system.
- Firmware Rootkits – These kits overwrite the PC’s basic input/output system firmware or other hardware so that the rootkit can start before Windows wakes up.
- Driver Rootkits – At the driver level, applications can have full access to system hardware. Thus, this kit claims to be one of the trusted drivers that Windows uses to communicate with PC hardware.
- Starter Kits – It is an advanced form of rootkits that takes the basic functionality of a rootkit and extends it with the ability to infect the Master Boot Record (MBR). It replaces the operating system boot loader so that the PC loads the Bootkit before the operating system.
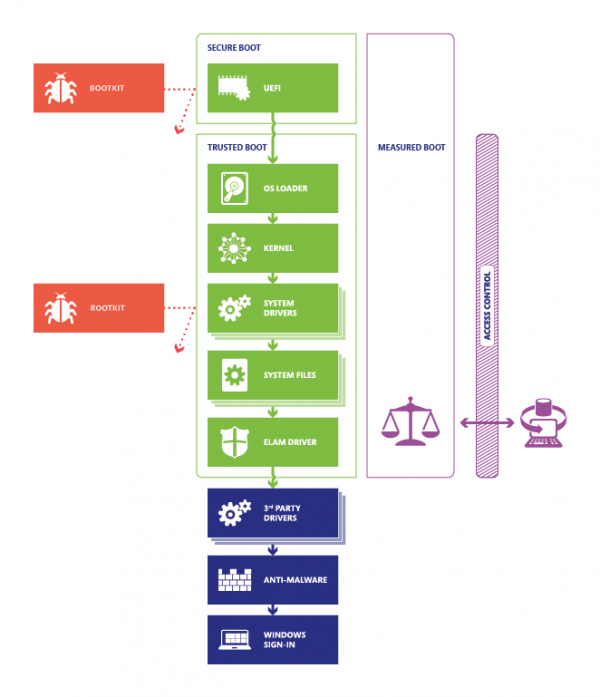
Windows 10 has 4 features that secure the Windows 10 boot process and avoid these threats.
Securing the Windows Boot Process
Secure Boot
Secure Boot is a security standard developed by members of the computer industry to help protect your system from malware by preventing unauthorized applications from running during the system boot process. The feature ensures that your PC only boots using software approved by the PC manufacturer. So every time your PC boots, the firmware checks the signature of every bootable software, including firmware drivers (optional ROMs) and the operating system. If the signatures are verified, the PC boots and the firmware gives control to the operating system.
Trusted start
This boot loader uses the Virtual Trusted Platform Module (VTPM) to verify the digital signature of the Windows 10 kernel before loading it, which in turn verifies all other components of the Windows boot process, including boot drivers , boot files and ELAM. If a file has been tampered with or modified in any way, the bootloader detects it and refuses to load it recognizing it as a corrupt component. In short, it provides a chain of trust for all components during startup.
Early-Launch Antimalware
Early launch anti-malware (ELAM) protects computers on a network during startup and before third-party drivers are initialized. After Secure Boot successfully protects the boot loader and Trusted Boot completes/completes the Windows kernel backup task, ELAM’s role begins. It closes any loophole left for malware to boot or initiate an infection by infecting a non-Microsoft boot driver. The feature immediately loads Microsoft or non-Microsoft anti-malware. This helps establish a continuous chain of trust established by Secure Boot and Trusted Boot, earlier.
Measured boot
It has been observed that PCs infected with rootkits continue to look healthy even with running anti-malware. These infected PCs, if connected to a corporate network, pose a serious risk to other systems by opening up pathways for rootkits to access large amounts of confidential data. Measured Boot in Windows 10 allows a trusted server on the network to verify the integrity of the Windows boot process using the following processes.
- Running a non-Microsoft remote attestation client – The trusted attestation server sends the client a unique key at the end of each boot process.
- The PC’s UEFI firmware stores in the TPM a hash of the firmware, bootloader, bootable drivers and anything that will be loaded before the anti-malware application.
- The TPM uses the unique key to digitally sign the UEFI recorded log. The client then sends the log to the server, possibly with other security information.
With all this information at hand, the server can now determine if the client is healthy and grant the client access to a limited quarantine network or the full network.
Read all the details at Microsoft.
