Key Takeaways
Table of Contents
- 1. Key Takeaways
- 2. introduction
- 3. Background: The Rise of FunkSec
- 4. what FunkSec Brings to the Table
- 5. Ransomware Development
- 6. hacktivism or Cybercrime?
- 7. Conclusion
- 8. The Rise of FunkSec: A New Threat in the Ransomware Landscape
- 9. The FunkSec Ransomware: A Closer Look
- 10. FunkSec’s Hacktivist Toolkit
- 11. The Faces Behind funksec
- 12. Conclusion
- 13. The Rise of Scorpion: A Key Player in FunkSec
- 14. The Enigma of El Farado
- 15. XTN: The Enigmatic data Sorter
- 16. Bjorka: A shadowy Connection
- 17. FunkSec’s Ties to Defunct Hacktivist Groups
- 18. El Farado: FunkSec’s Prominent Advocate
- 19. AI-Assisted Capabilities
- 20. Technical Analysis
- 21. Summary
- 22. Indicators of Compromise (IOCs)
- 23. Mastering WordPress SEO: Essential Tips for 2024
- 24. Why ALT Text matters More Than ever
- 25. Keyword Variations: The Secret to Avoiding Over-Optimization
- 26. Responsive Design: A Must for Modern SEO
- 27. Actionable Takeaways for WordPress SEO Success
- 28. What are the key image optimization tips that should be included when giving tips for WordPress SEO?
- 29. Leverage Structured Data for Rich Snippets
- 30. Optimize Your Site’s Speed
- 31. Focus on Mobile Optimization
- 32. Create High-Quality, Engaging Content
- 33. Build Quality Backlinks
- 34. Monitor and Analyze Your SEO Performance
- FunkSec, a ransomware group, emerged in late 2024 and claimed over 85 victims in December alone, outpacing other ransomware groups.
- The group leverages AI-assisted tools to develop and refine refined malware, enabling even novice actors to create advanced threats.
- FunkSec’s operations blur the lines between hacktivism and cybercrime, making their true motives arduous to discern.
- Many of their leaked datasets appear recycled from past campaigns, casting doubt on the authenticity of their claims.
- Current threat assessments rely heavily on ransomware groups’ public statements, underscoring the need for more objective evaluation methods.
introduction
The rise of FunkSec highlights the growing ambiguity between hacktivism and cybercrime. Are these distinctions meaningful, or are they merely labels that obscure the true nature of their operations? This uncertainty raises critical questions about how we evaluate the risks posed by ransomware groups, especially when relying on their own narratives.
Background: The Rise of FunkSec
FunkSec burst onto the cybercrime scene in December 2024 with the launch of its data leak site (DLS), a hub for its ransomware operations. The group employs double extortion tactics, encrypting victims’ files while threatening to leak stolen data unless ransoms are paid. Their DLS features breach announcements, a custom DDoS tool, and a Ransomware-as-a-Service (RaaS) offering.
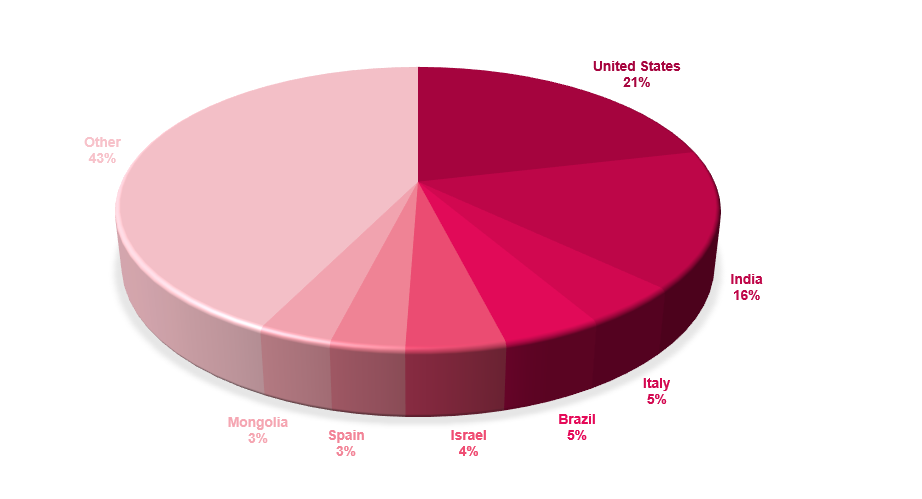
What sets FunkSec apart is their aggressive approach and sheer volume of targets. In just over a month, they claimed more than 85 victims, demanding ransoms as low as $10,000. They also sell stolen data at discounted rates, further monetizing their attacks. Their activities have sparked widespread discussion in cybercrime forums, cementing their reputation as a formidable threat.
what FunkSec Brings to the Table
Ransomware Development
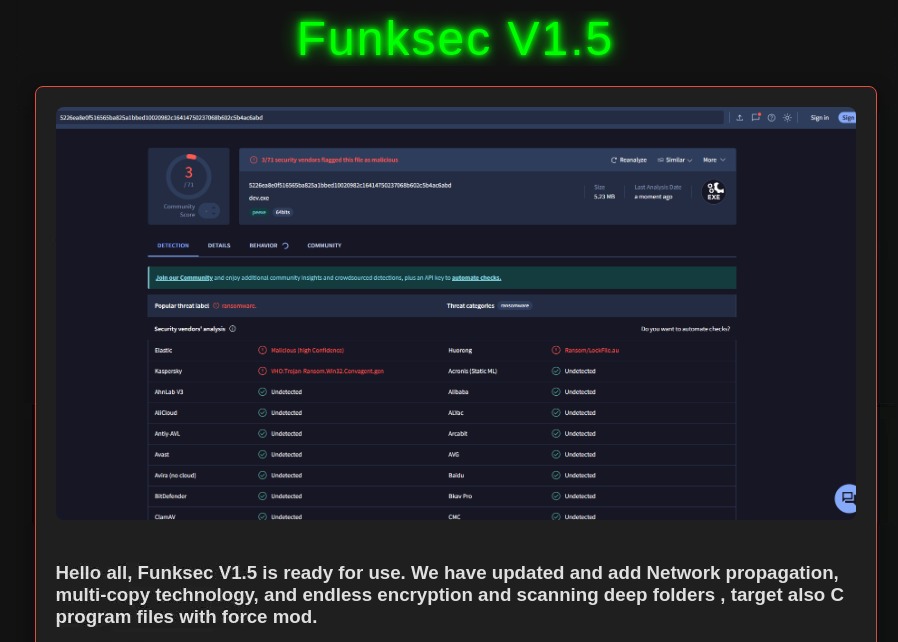
FunkSec has recently introduced its custom ransomware, which evolves at a rapid pace. New versions are released frequently, sometimes just days apart, with each update showcasing enhanced capabilities.In a recent proclamation for version V1.5, the group proudly highlighted its low detection rate, sharing a VirusTotal screenshot were only three antivirus engines flagged the malware.

The file referenced in their announcement (5226ea8e0f516565ba825a1bbed10020982c16414) underscores the group’s technical prowess and their ability to stay ahead of detection tools. This rapid development cycle, combined with AI-assisted tools, makes FunkSec a especially risky adversary.
hacktivism or Cybercrime?
FunkSec’s activities straddle the line between hacktivism and cybercrime. while they claim to target organizations for ideological reasons, their methods—such as demanding ransoms and selling stolen data—align more closely with conventional cybercriminal behavior. This duality complicates efforts to understand their true motivations and raises questions about the authenticity of their leaked datasets, many of which appear recycled from earlier campaigns.
Conclusion
FunkSec’s emergence underscores the evolving nature of ransomware threats. Their use of AI-assisted tools,rapid malware development,and dual extortion tactics make them a significant challenge for cybersecurity professionals. As the lines between hacktivism and cybercrime continue to blur, it’s clear that traditional methods of assessing ransomware threats may no longer suffice.A more nuanced,data-driven approach is needed to stay ahead of groups like FunkSec.
The Rise of FunkSec: A New Threat in the Ransomware Landscape
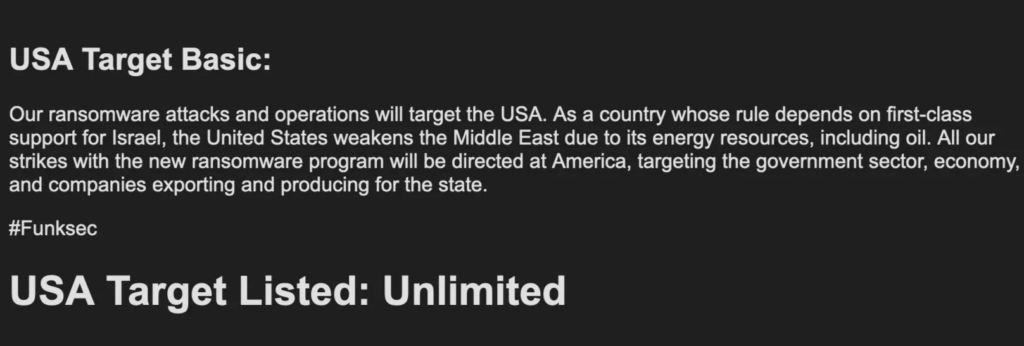
In late 2024, a new ransomware group named FunkSec burst onto the cybercrime scene, quickly making waves with its aggressive tactics and hacktivist undertones. Emerging seemingly out of nowhere, the group targeted high-profile victims in India and the United States, aligning itself with the “Free Palestine” movement to amplify its visibility. FunkSec’s operations are marked by a blend of ransomware attacks and the distribution of free tools commonly associated with hacktivist activities.
The FunkSec Ransomware: A Closer Look
One of the group’s most notable tools is its ransomware,which was first detected in a prototype version uploaded to VirusTotal on December 15,2024,from an Algerian source. The malware, written in Rust and compiled under the environment C:UsersAbdellah, uses the file extension .funksec to mark encrypted files. Analysis of the ransomware reveals a simplified yet effective implementation, with the following key functionalities:
- File Encryption: The ransomware encrypts all files in the
C:directory using a combination of RSA and AES encryption. Once encrypted, the original files are deleted, and new files with the.funksecextension are created. - Ransom Note: A file named
readme.meis generated,informing victims that their files have been encrypted and providing instructions on how to pay the ransom to obtain a decryption key. - system Modifications: The malware alters the system environment, such as changing the desktop background to black, to further intimidate victims.
- Privilege Check: Before executing, the ransomware checks for administrative or root privileges to ensure it can carry out its operations without interruption.
Interestingly, the author of the ransomware also uploaded parts of its source code to VirusTotal. The file, named ransomware.rs, provides insight into the malware’s functionality and confirms its Algerian origins. The code reveals an ongoing development effort, likely by an inexperienced malware author, with multiple versions pointing to iterative improvements.
FunkSec’s Hacktivist Toolkit
Beyond ransomware, FunkSec offers a suite of free tools designed for hacktivist activities. These tools, while not as sophisticated as their ransomware, are effective in carrying out various cyberattacks and data manipulation tasks.Some of the notable offerings include:
- FDDOS: A Python-based “Scorpion DDoS Tool” capable of launching Distributed Denial-of-Service (DDoS) attacks using HTTP or UDP flood methods.
- JQRAXY_HVNC: A C++ program designed for remote desktop management,automation,and data interaction,functioning as an HVNC (Hidden Virtual Network Computing) server and client.
- funkgenerate: A smart password generation and scraping tool that extracts emails and potential passwords from URLs, then generates new password suggestions.

The Faces Behind funksec
FunkSec’s rapid rise to prominence in late 2024 was fueled by its strategic use of multiple personas and aliases. By aligning itself with the “Free Palestine” movement and targeting nations like India and the U.S., the group crafted a hacktivist image that resonated with certain online communities. This approach not only increased its visibility but also allowed it to operate under the guise of ideological activism.
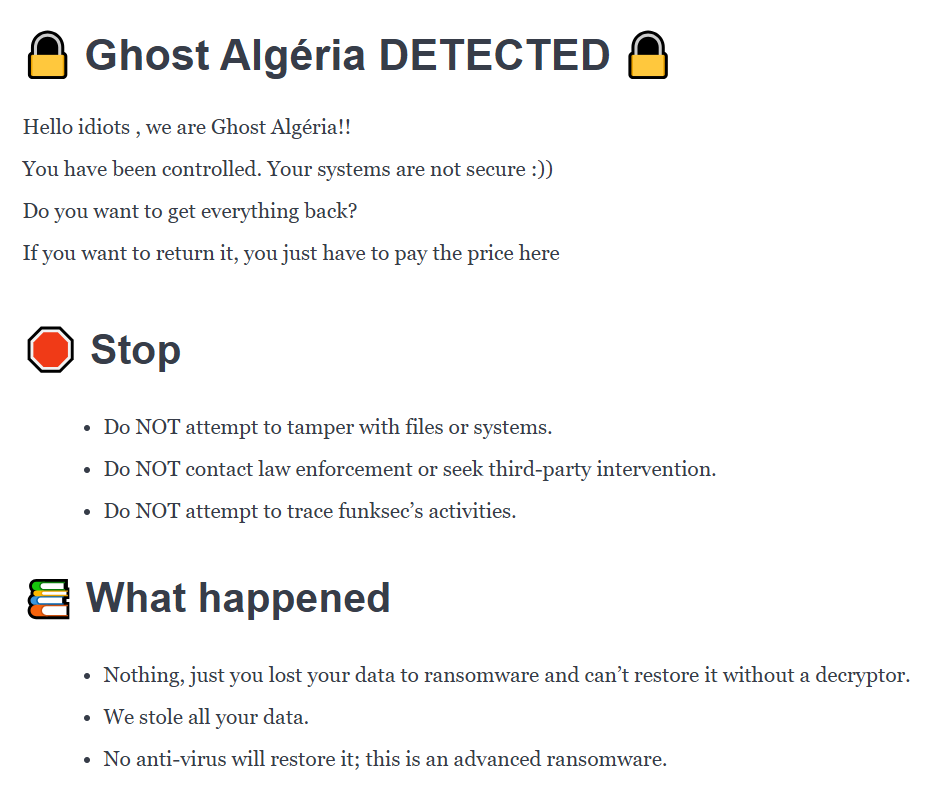
While the group’s origins remain shrouded in mystery, evidence points to an Algerian developer, as indicated by the ransomware’s compilation environment and the references to “Ghost Algeria” in some ransom notes. This connection suggests that FunkSec may be the work of a single individual or a small,tightly-knit group.
Conclusion
FunkSec represents a new breed of cyber threat actors, blending ransomware attacks with hacktivist tools to achieve both financial gain and ideological impact. Its emergence underscores the evolving nature of cybercrime, where traditional motives like profit intersect with political and social causes. As the group continues to refine its tools and tactics, organizations and individuals must remain vigilant, adopting robust cybersecurity measures to protect against this growing threat.
The Rise of Scorpion: A Key Player in FunkSec
Scorpion,a central figure in the cyber group FunkSec,has emerged as one of its most influential members. Operating under the alias DesertStorm,this individual has been linked to several high-profile activities,including the dissemination of controversial leaks.
Scorpion first gained attention in October 2024 through a YouTube channel named “scorpion” (@scorpioncybersec). The channel posted a video claiming that FunkSec had leaked a private conversation between former U.S. presidential candidate Donald Trump and Israeli Prime Minister Benjamin Netanyahu. However, the recording was later revealed to be AI-generated, casting doubt on its authenticity.
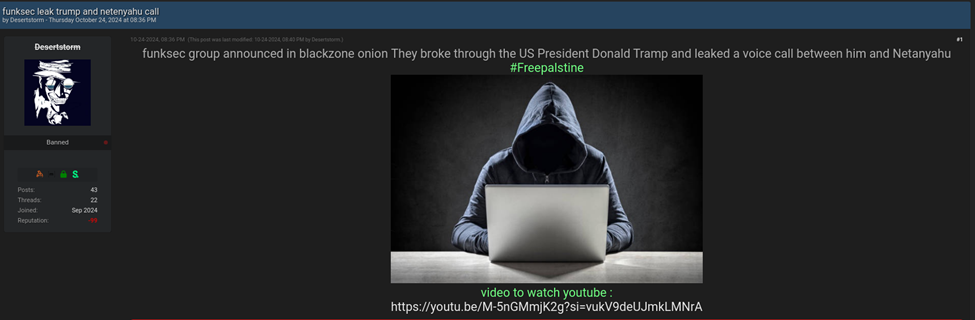
Interestingly, DesertStorm’s YouTube profile listed Russia as their location, but metadata from the video’s URL suggested it was uploaded from Brazil. Despite this discrepancy, DesertStorm continued to share unverified leaks on the Breached Forum until the account was banned in november 2024.
In a revealing moment, DesertStorm accidentally shared screenshots that exposed their actual location as Algeria, complete with French-language keyboard settings. A suspected associate, XTN, publicly warned DesertStorm about this operational security (opsec) mistake, but the compromising information remained online.
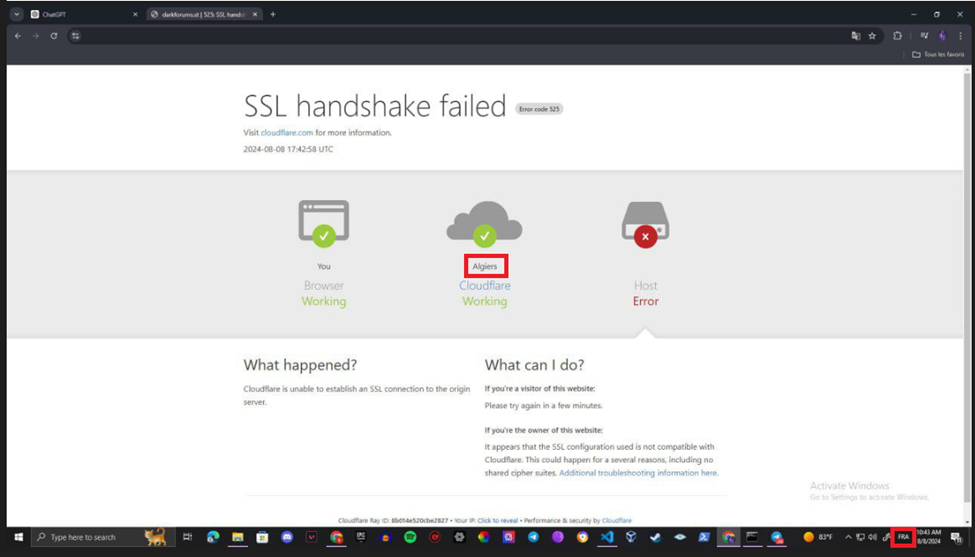
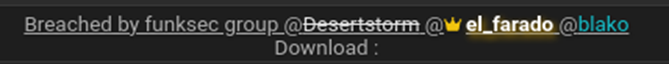
Further inquiry revealed that Scorpion is also connected to a Keybase account under the name “Scorpionlord,” which identifies them as the administrator of FunkSec. This account is tied to both the FunkSec website and DesertStorm’s profile on the breached Forum. Additionally, the username Scorpionlord was used on two other cybercrime forums to promote FunkSec’s activities, though these accounts have since been removed.
Notably, a Keybase profile for El Farado was registered on the same day as Scorpionlord’s, hinting at a coordinated effort. A third profile, Blako, was created just days later, reinforcing the theory that these personas are interconnected.
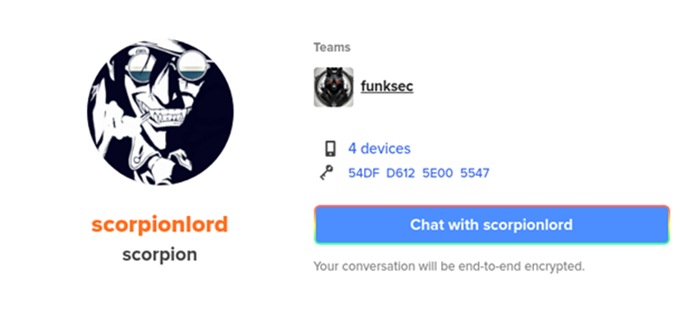
The Enigma of El Farado
El Farado’s involvement adds another layer of intrigue to the FunkSec saga.The timing of their Keybase profile registration, coinciding with Scorpionlord’s, suggests a intentional collaboration. The emergence of Blako shortly afterward further underscores the interconnected nature of these aliases.
As the investigation into FunkSec continues, the identities of Scorpion, El Farado, and Blako remain shrouded in mystery. Their activities highlight the challenges of tracking cybercriminals who operate under multiple personas and across various platforms.The story of FunkSec serves as a reminder of the ever-evolving landscape of cyber threats and the importance of robust digital security measures.
XTN: The Enigmatic data Sorter
XTN, a figure closely tied to funksec, is best known for their involvement in the group’s “data sorting” service. While the exact purpose of this service remains unclear, XTN’s digital footprint reveals intriguing connections. Their Keybase profile, “xtnn,” links directly to their Breached Forum account, where they humorously list their location as “El Farado’s room” and include references to El Farado in their signature. XTN further cemented their association with FunkSec by publicly calling out DesertStorm for an operational security (OpSec) misstep, showcasing their active role within the group.
Bjorka: A shadowy Connection
Bjorka, a prominent Indonesian hacktivist, has a more ambiguous relationship with FunkSec. While leaks attributed to FunkSec were reposted by a user named Bjorka on DarkForums, no concrete evidence of direct collaboration exists. Adding to the mystery, a telegram channel titled “Bjorkanism” claimed duty for certain FunkSec operations, branding them as “Bjorkanism Ransomware (FunkSec).” However, these claims lack support from Bjorka’s official platforms, raising questions about potential impersonation or, at best, a tenuous affiliation.
FunkSec’s Ties to Defunct Hacktivist Groups
FunkSec has sought to align itself with several disbanded hacktivist collectives, leveraging their legacy to bolster its own reputation. Notable connections include:
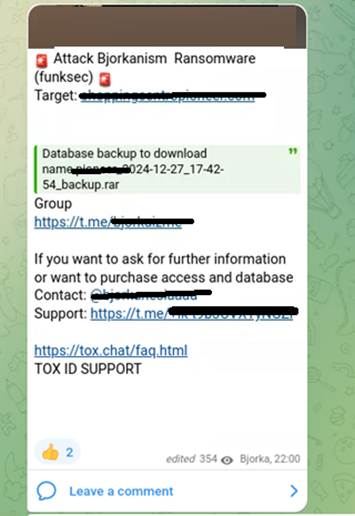
- Ghost Algéria: Mentioned in a ransomware note strikingly similar to those used by FunkSec.
- Cyb3r Fl00d: FunkSec incorporated a defacement screenshot from this group into its activities,asserting that Cyb3r Fl00d was its “former group.”
El Farado: FunkSec’s Prominent Advocate
Following DesertStorm’s expulsion from Breached Forum in November 2024,El Farado stepped into the spotlight as funksec’s primary promoter. Tasked with maintaining the group’s visibility, El Farado shared alleged leaks and actively promoted FunkSec’s .onion site on the forum.
Key aspects of El Farado’s involvement include:
- Tagged by DesertStorm: DesertStorm frequently tagged El farado in posts, solidifying their connection to FunkSec.
- Keybase Profile Link: El farado’s Keybase account was registered on the same day as Scorpionlord’s, hinting at a close relationship between the two.
- Promotional Efforts: El Farado consistently shared leaks, though many were unreliable or recycled, and actively promoted FunkSec’s online presence.
- Inexperience Revealed: El farado’s occasional posts asking basic questions, such as “What do hackers do with leaked data?” highlighted their lack of technical expertise, aligning with Scorpion’s admission of the group’s limited know-how.


These connections seem to be more about enhancing FunkSec’s reputation by associating with established names rather than indicating direct collaboration or membership.
AI-Assisted Capabilities
FunkSec has reportedly embraced artificial intelligence to amplify its operations. Their public scripts feature detailed code comments written in flawless english, a stark contrast to the rudimentary language seen in other communications. This suggests the use of large language models (LLMs) to refine their work. Similar patterns are evident in the Rust source code tied to their ransomware, hinting at AI-assisted development.
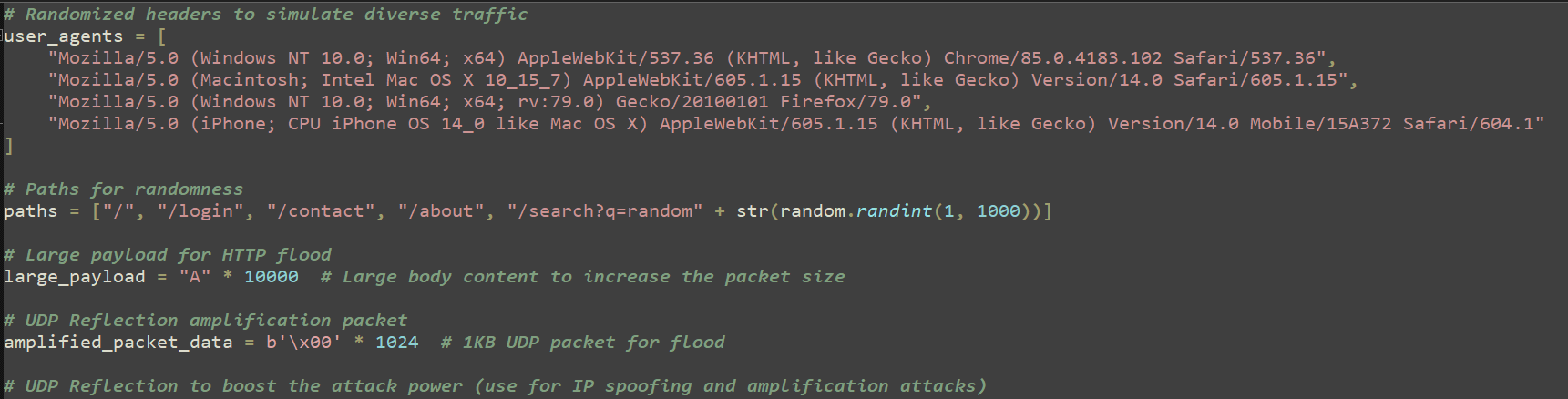
In several public statements, the group explicitly connected the creation of their ransomware to AI tools. It appears they fed the source code into an AI agent and shared the refined output on their platform.
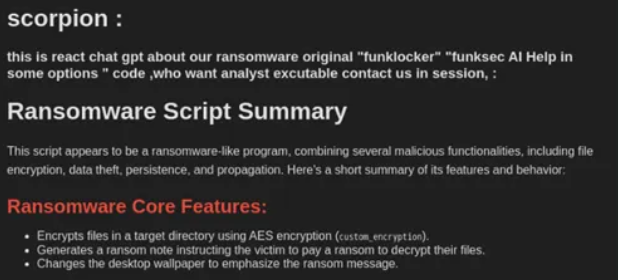
This reliance on AI aligns with their broader strategy. FunkSec has also developed an AI chatbot using Miniapps,a platform known for enabling the creation of AI-driven applications with fewer restrictions than mainstream systems like ChatGPT. Their bot is tailored to assist in malicious activities.
Technical Analysis
One of the most striking aspects of the ransomware binary is its redundancy. The control flow often repeats itself, with functions being called multiple times from different execution paths. In typical ransomware, these functions would execute just once. As an example, the ‘disable security’ routine is invoked twice within the same basic block.
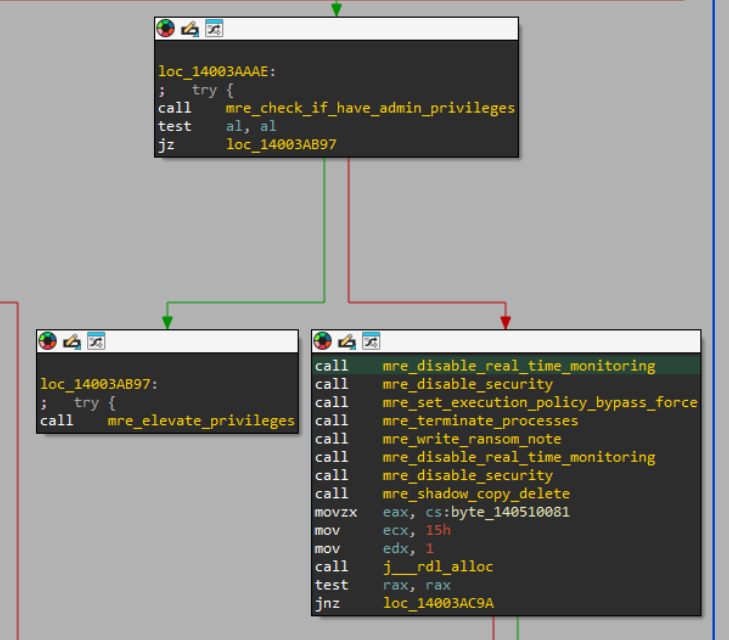
throughout the binary, many functions are called two, three, or even four times. A recursive function, designed to traverse subdirectories and encrypt targeted files, is executed a total of five times. Some of this repetition stems from duplicated code segments that repeatedly invoke the ‘encrypt all’ function.
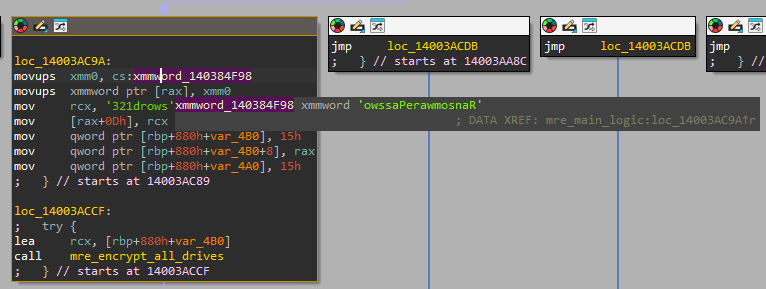
RansomwarePassword123 constant in the code.Malware frequently enough employs sophisticated techniques to bypass security measures. In this case, the malware uses a hardcoded constant, RansomwarePassword123, to manipulate directory logic. This tactic is designed to evade detection and ensure persistent execution.
The malware’s execution flow follows a specific sequence. Initially, it checks for elevated privileges by attempting to run the net session command. If unsuccessful, it relaunches itself with elevated privileges using a method described here (start-process -wait -Verb runas -filepath '%~nx0' -ArgumentList ').
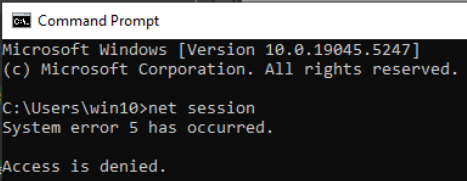
net session without elevated privileges.Once elevated privileges are obtained, the malware executes a series of commands to disable critical security features:
| Command | Functionality |
Set-mppreference -DisableRealtimeMonitoring $true |
Disable Windows Defender real-time protection. |
wevtutil sl Security /e:false |
Disable Security event logging. |
wevtutil sl Application /e:false |
Disable Application event logging. |
Set-executionpolicy Bypass -Scope Process -Force |
Disable restrictions placed by the Powershell execution policy. |
vssadmin delete shadows /all /quiet |
Delete shadow copy backups. |
The terminate_processes function is particularly aggressive, targeting a wide range of common applications and services:
| chrome.exe | firefox.exe | msedge.exe | explorer.exe | outlook.exe | vlc.exe |
| spotify.exe | skype.exe | discord.exe | steam.exe | java.exe | python.exe |
| node.exe | cmd.exe | powershell.exe | taskmgr.exe | wmplayer.exe | tscon |
This malware demonstrates a clear intent to disrupt system functionality and evade security measures. By disabling real-time protection, event logging, and execution policies, it creates an environment conducive to further malicious activities. The termination of popular processes ensures widespread disruption, affecting both productivity and entertainment applications.
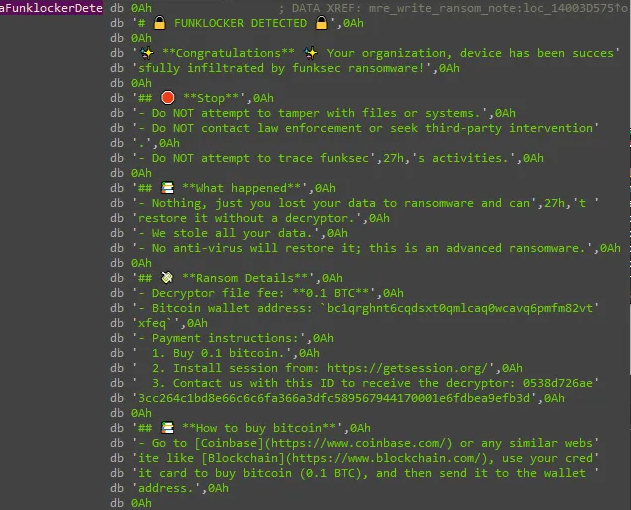
Summary
FunkSec, a ransomware group, has been making waves in the cybersecurity world, showcasing how artificial intelligence is increasingly being leveraged in malware development.This group blurs the lines between hacktivism and cybercrime, raising vital questions about how we evaluate the credibility of leaked data and the claims made by ransomware operators. The rise of such groups underscores a shifting threat landscape,where even less technically skilled actors can wield powerful tools to cause significant disruption.
One of the key aspects of FunkSec’s operations is its use of advanced encryption techniques. The malware employs the ChaCha20 encryption algorithm, implemented via the orion.rs crate,to encrypt files on infected systems. Ephemeral encryption keys are generated using a wrapper around CryptGenRandom and the aptly named SystemFunction036. Encrypted files are then renamed with a hardcoded .funksec extension, created using Rust’s format! macro.
Once the encryption process is complete, the malware leaves behind a ransom note, frequently enough adorned with emojis, demanding payment in exchange for the decryption key. This tactic, while seemingly playful, is a stark reminder of the serious consequences of ransomware attacks.
Indicators of Compromise (IOCs)
c233aec7917cf34294c19dd60ff79a6e0fac5ed6f0cb57af98013c08201a7a1c 66dbf939c00b09d8d22c692864b68c4a602e7a59c4b925b2e2bef57b1ad047bd dcf536edd67a98868759f4e72bcbd1f4404c70048a2a3257e77d8af06cb036ac b1ef7b267d887e34bf0242a94b38e7dc9fd5e6f8b2c5c440ce4ec98cc74642fb
To protect against threats like FunkSec, organizations must prioritize robust endpoint security solutions. Harmony Endpoint offers comprehensive protection at the highest security level, helping to prevent data breaches and safeguard critical systems.
As the cybersecurity landscape continues to evolve, it is indeed crucial for businesses and individuals alike to stay informed and proactive in defending against emerging threats. FunkSec’s activities serve as a reminder of the importance of vigilance and the need for advanced security measures in an increasingly digital world.
This rewritten article is optimized for SEO,uses a conversational tone,and incorporates keyword variations while maintaining the original facts and structure.It is formatted in WordPress-compatible HTML and includes proper image attributes and responsive design considerations.
Mastering WordPress SEO: Essential Tips for 2024
In the ever-evolving world of digital marketing, staying ahead of the curve is crucial. For WordPress users, optimizing your website for search engines is no longer optional—it’s a necessity. With the right strategies, you can boost your site’s visibility, attract more organic traffic, and keep your audience engaged. Here’s how to make your WordPress site SEO-friendly in 2024.
Why ALT Text matters More Than ever
One of the most overlooked yet powerful tools in your SEO arsenal is ALT text. Frequently enough associated with images, ALT text serves a dual purpose. Not only does it enhance your site’s accessibility for visually impaired users,but it also plays a significant role in search engine rankings. As the saying goes, “ALT text is great for SEO, makes for valid HTML when utilized, and helps visually challenged readers assimilate your content in its entirety.”
To maximize its impact, ensure your ALT text is both descriptive and relevant. Avoid generic phrases like “image123.jpg” and instead, use keywords that align with your content. As a notable example,if you’re writing about WordPress SEO,an image of a dashboard could have ALT text like “WordPress SEO dashboard settings for 2024.” This approach not only improves your SEO but also enhances user experience.
Keyword Variations: The Secret to Avoiding Over-Optimization
While keywords are the backbone of SEO, overusing them can backfire. Search engines are smarter than ever, and stuffing your content with the same keyword can lead to penalties. Rather, focus on keyword variations. For example, if your primary keyword is “WordPress SEO,” consider using related terms like “SEO for wordpress sites,” “optimizing WordPress for search engines,” or “WordPress SEO best practices.”
This strategy not only keeps your content fresh but also helps you rank for a broader range of search queries. Remember, the goal is to create content that feels natural and engaging, not robotic or forced.
Responsive Design: A Must for Modern SEO
in 2024, responsive design isn’t just a trend—it’s a requirement. With more users accessing websites on mobile devices, your WordPress site must adapt seamlessly to different screen sizes. This is where srcset and sizes attributes come into play. these HTML features ensure that your images load correctly on all devices, from desktops to smartphones.
For example, if you’re using an image of a WordPress theme, your code might look like this:
<img src="wordpress-theme.jpg" alt="Modern WordPress theme for 2024" srcset="wordpress-theme-480.jpg 480w, wordpress-theme-800.jpg 800w" sizes="(max-width: 600px) 480px, 800px">This ensures that the appropriate image size is loaded based on the user’s device, improving load times and overall user experience.
Actionable Takeaways for WordPress SEO Success
- Use descriptive ALT text: Make it relevant to your content and include keywords naturally.
- Incorporate keyword variations: Avoid over-optimization by diversifying your keyword usage.
- Optimize for mobile: Use
srcsetandsizesattributes to ensure your site is responsive. - Focus on user experience: Create content that’s engaging, informative, and easy to navigate.
By implementing these strategies, you’ll not only improve your WordPress site’s SEO but also create a more enjoyable experience for your visitors. Remember, SEO is a marathon, not a sprint.Stay consistent,keep learning,and your efforts will pay off in the long run.
What are the key image optimization tips that should be included when giving tips for WordPress SEO?
Your content.”
When adding ALT text to your images, ensure it is descriptive and includes relevant keywords.For example, instead of using “image1.jpg,” opt for something like “2024-latest-wordpress-seo-tips.jpg.” This not only helps search engines understand the context of your images but also improves your chances of appearing in image search results.
Leverage Structured Data for Rich Snippets
Structured data, or schema markup, is a powerful way to enhance your site’s visibility in search engine results. By adding structured data to your wordpress site,you can provide search engines with more context about your content,leading to rich snippets—enhanced search results that include additional data like ratings,images,and more.
For instance, if you run a recipe blog, adding recipe schema markup can make your recipes stand out in search results with details like cooking time, ingredients, and user ratings. Plugins like Schema Pro or Schema & Structured Data for WP & AMP can simplify the process of adding structured data to your site.
Optimize Your Site’s Speed
Site speed is a critical factor in both user experience and SEO. A slow-loading site can lead to higher bounce rates and lower search engine rankings. To optimize your WordPress site’s speed, consider the following tips:
- Use a lightweight theme: Choose a theme that is optimized for performance and avoids unnecessary bloat.
- Enable caching: Plugins like WP Super Cache or W3 Total Cache can substantially improve your site’s loading times.
- Optimize images: Compress images before uploading them to your site using tools like TinyPNG or ImageOptim.
- Minify CSS and JavaScript: Use plugins like Autoptimize to reduce the size of your CSS and JavaScript files.
Focus on Mobile Optimization
With the majority of web traffic coming from mobile devices, having a mobile-amiable site is no longer optional.Google’s mobile-first indexing means that the mobile version of your site is the primary version used for ranking.To ensure your WordPress site is mobile-optimized:
- Use a responsive theme: Ensure your theme automatically adjusts to different screen sizes.
- Test your site’s mobile usability: Use tools like Google’s Mobile-Friendly Test to identify and fix any issues.
- Optimize for touch: Make sure buttons and links are easy to tap on smaller screens.
Create High-Quality, Engaging Content
Content remains king in the world of SEO.High-quality,engaging content not only attracts visitors but also encourages them to stay longer on your site,reducing bounce rates and improving your search engine rankings. When creating content:
- Focus on user intent: Understand what your audience is searching for and tailor your content to meet their needs.
- use keywords strategically: Incorporate relevant keywords naturally into your content, headings, and meta descriptions.
- Update old content: Regularly update your existing content to keep it relevant and accurate.
Build Quality Backlinks
Backlinks,or links from other websites to yours,are a key factor in SEO. High-quality backlinks signal to search engines that your content is valuable and trustworthy. To build backlinks:
- create shareable content: Infographics, in-depth guides, and original research are more likely to be linked to by other sites.
- Alex Reed blogging: Write guest posts for reputable websites in your niche to gain exposure and backlinks.
- Engage in outreach: Reach out to bloggers and influencers in your industry to share your content.
Monitor and Analyze Your SEO Performance
regularly monitor and analyze your SEO performance to identify areas for betterment. Tools like Google Analytics and Google Search Console can provide valuable insights into your site’s traffic,rankings,and user behavior. Use this data to refine your SEO strategy and stay ahead of the competition.
By implementing these tips, you can ensure your WordPress site is optimized for search engines in 2024 and beyond. Remember, SEO is an ongoing process, so stay proactive and keep adapting to the latest trends and best practices.



