2024-12-06 23:11:00
 macOS” style=”margin: auto;margin-bottom: 5px;max-width: 100%” />
macOS” style=”margin: auto;margin-bottom: 5px;max-width: 100%” />
More than a year after we talked about the malware Realsteverything indicates that he is active again in a new guise. This time, disguised as a video conferencing app to steal user data.
As discovered by Cado Securitythe newest campaign targets people looking for jobs at Web3 1 companies, who receive a link to a site that supposedly offers meeting software for macOS or Windows.
Related Posts
- “Stealer” malware was the most common threat on Mac in 2024
- North Korean app with malicious code can bypass macOS security
- But already? New attack tactic tries to bypass macOS 15 protections
This software, which may have names like “Meeten”, “Meetio” or “Clusee”, is actually malware capable of stealing keys stored on macOS, in data from Chromium-based browsers, Telegram or cryptocurrency wallets. popular.
When the user downloads the application, an error message appears and they are asked to enter the macOS administrator password — a strategy that is used to bypass the security measures adopted by Apple in the system.
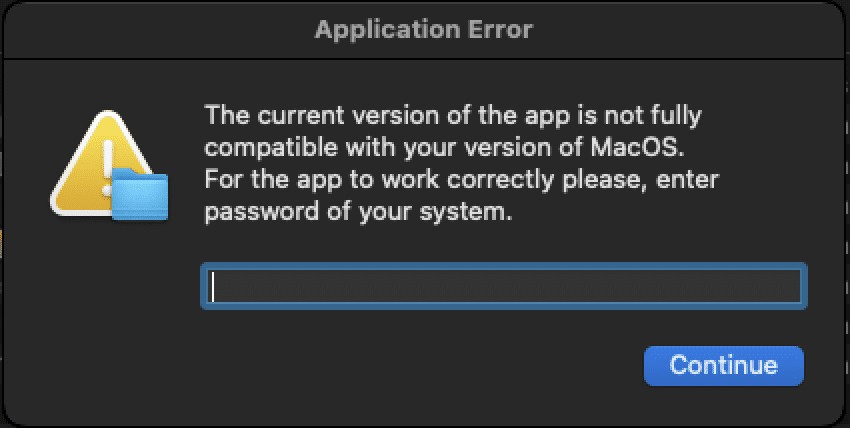
Once this is done, the app can steal data such as cookies from browsers, as well as login credentials, which can give access to platforms where multifactor authentication is not configured.
As protective measures, it is always worth trying your best not to download apps from unknown sources and, perhaps, even using software specialized in detecting and eliminating malware.
Footnotes
1733528646
#Realst #Stealer #malware #returns #macOS #disguised #meeting #apps
What specific tactics are used by the “Meeten” malware to deceive users into thinking it is legitimate video conferencing software?
## On the Rise: Malware Masquerading as Video Conferencing Software
**Host:** Welcome back to Tech Tonight. Tonight we’re discussing a new cybersecurity threat targeting job seekers in the Web3 sector. Joining me is cybersecurity expert, [Guest Name], to shed light on this dangerous new malware.
**Guest:** Thanks for having me. This malware, dubbed “Meeten” by researchers at Cado Security, is particularly insidious because it masquerades as legitimate video conferencing software. [[]](https://macmagazine.com.br/2024/12/06/malware-disfarcado-de-aplicativo-de-video-conferencia-alvo-profissionais-web3/)
**Host:** So, how does it work?
**Guest:** Potential victims, often those searching for jobs in Web3 companies, receive a link to a website offering this seemingly helpful meeting software. It’s available for both macOS and Windows operating systems. However, once downloaded and installed, the software begins stealing sensitive user data like passwords, financial information, and even cryptocurrency wallets. [[]](https://macmagazine.com.br/2024/12/06/malware-disfarcado-de-aplicativo-de-video-conferencia-alvo-profissionais-web3/)
**Host:** That sounds alarmingly similar to a previous malware strain called Realst.
**Guest:** Indeed, there are definitely similarities. It seems Realst has reappeared, albeit in a cleverly disguised form. This highlights the ever-evolving nature of cyber threats and the importance of vigilance.
[[]](https://macmagazine.com.br/2024/12/06/malware-disfarcado-de-aplicativo-de-video-conferencia-alvo-profissionais-web3/)
**Host:** What can viewers do to protect themselves from this threat?
**Guest:** Always be cautious when downloading software from unknown sources. Verify the legitimacy of the website and software before installing anything. Look for reviews and ratings from trusted sources.
**Host:** Excellent advice. Thank you for joining us, [Guest Name], and shedding light on this important issue.
**Guest:** My pleasure. Stay safe online!
