AI Image Generators: The Unwelcome Hackers!
Right, folks, buckle up! We’ve got a classic case of good ol’ cyber deception right in our backyard! It seems that while we’ve been busy crafting our most fabulous memes and deepfake TikToks, some cheeky hackers have decided to dress up their malware in a shiny new AI costume. I mean, who wouldn’t want to download a program that promises to make you a digital Picasso, only to find it’s more of a digital parasite?
Fake AI Image Generators Push Lumma Stealer
Over just the past month, the digital chameleons behind this malware have been churning out fake websites that clumsily impersonate a shiny AI video and image editor, dubbed EditPro. Their marketing strategy? Advertisements promoting deepfake videos of political heavyweights like President Biden and Trump enjoying, wait for it… ice cream together. Nothing screams legitimacy quite like a video of two statesmen licking cones! 🥴
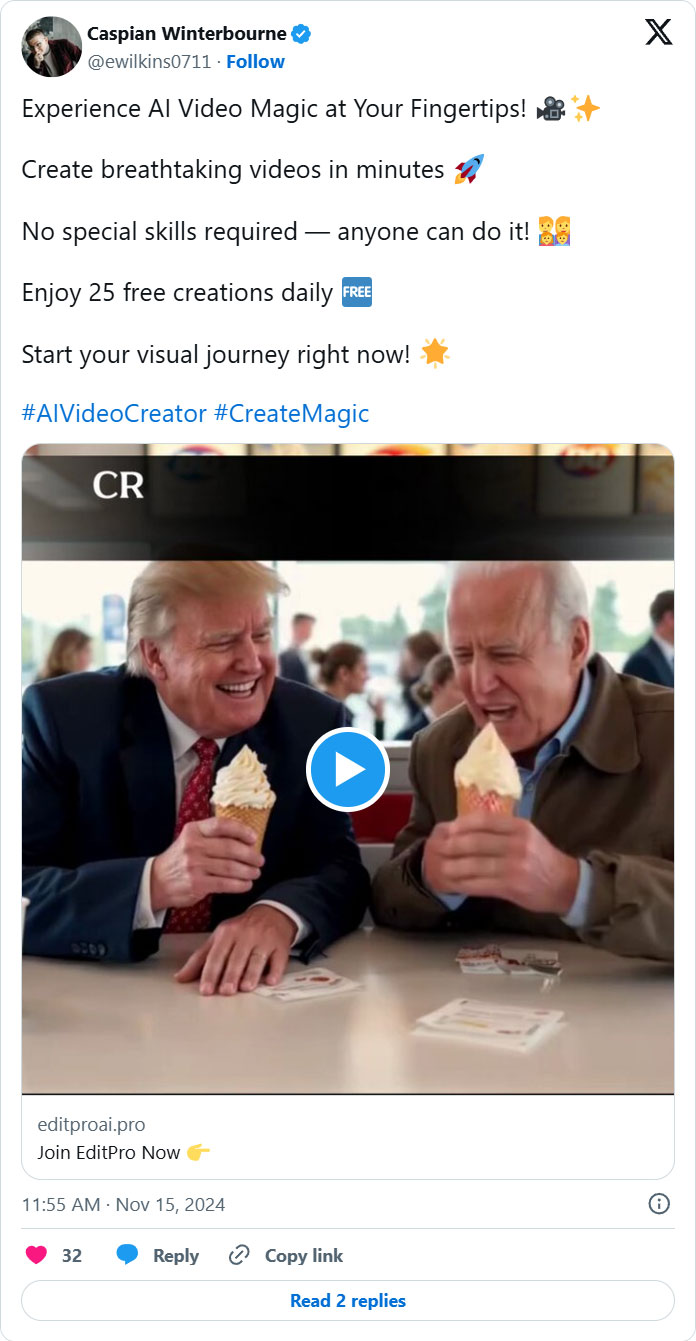
Source: BleepingComputer.com
But clicking on their dazzling images will lead you to a web of deceit! The pages look so real, they might even convince your skeptical grandmother. You’ve got cookie banners, usage statistics, and perhaps even a partridge in a pear tree. But when you hit that “Get Now” button, instead of the AI miracle you envisioned, you’re graced with an executable file—the digital equivalent of inviting a vampire into your home! 🦇
The Windows version goes by the name Edit-ProAI-Setup-newest_release.exe, because if you’re going to trick people, it’s definitely best to sound as reliable as possible! Meanwhile, our macOS friends are offered EditProAi_v.4.36.dmg. A tip to all the Mac aficionados out there: if it sounds like a product from a dodgy back alley mechanic, it probably isn’t going to improve your performance. VirusTotal can help you out—but let’s be real, wouldn’t it be easier to just stick with what you know?
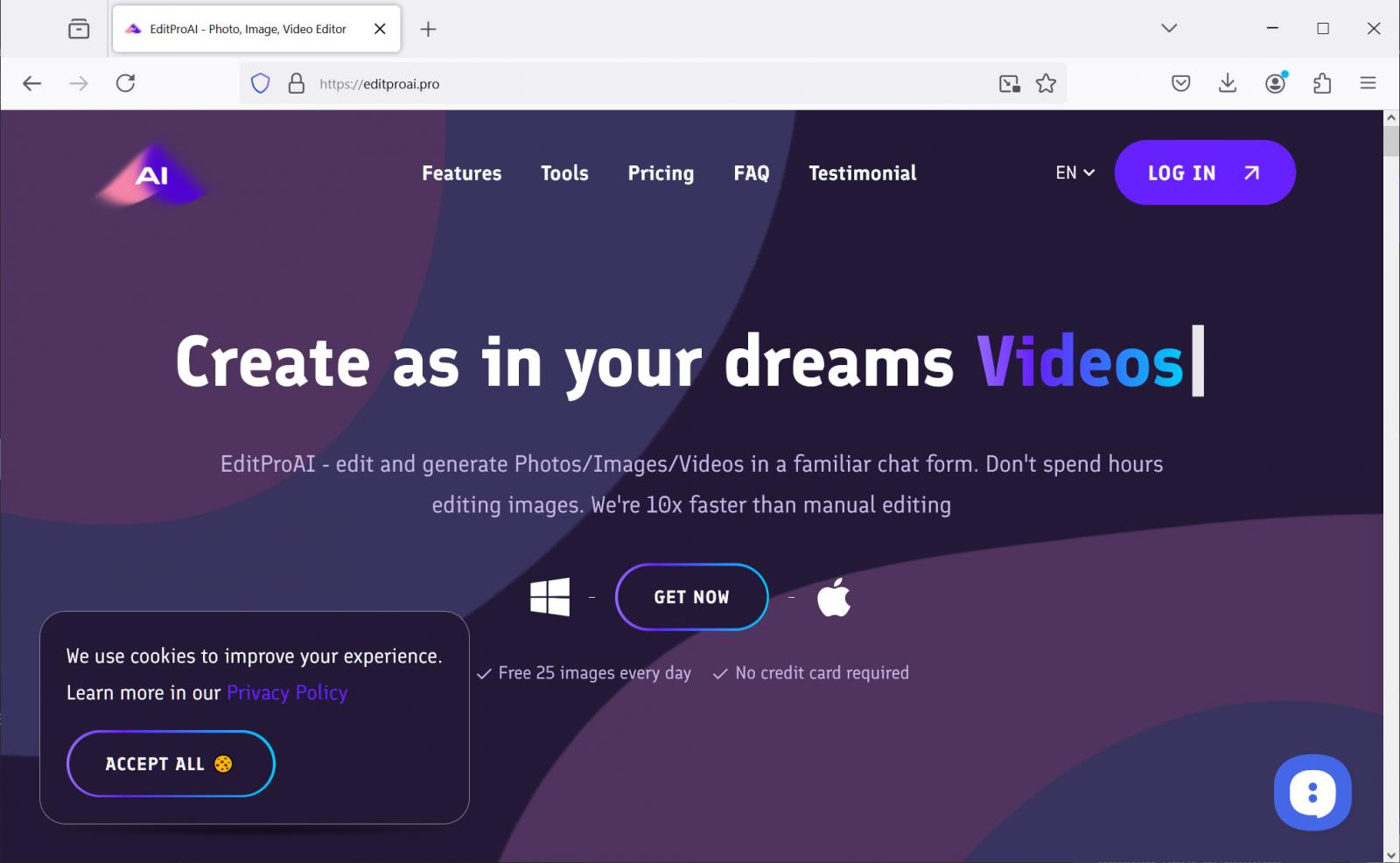
Source: BleepingComputer
Now, not only do we have beautiful fakes, but they’ve somehow managed to slap a stolen *code signing certificate* on the Windows malware, making it seem legit. It’s as if they took a degree in “How to Defraud People 101” from the University of Duplicity!
Once you inadvertently hand over your credentials, this little gem of malware sends your sensitive data to “proai[.]club/panelgood/”. Isn’t that cozy? That’s basically like handing your life savings to a scam artist while he compliments your choice in wardrobe. AnyRun report reveals this nasty little piece of work is, in fact, Lumma Stealer. So, if you’ve been seduced into downloading this fake software, it’s time to sweep and change those saved passwords like you’re competing in a password-resetting Olympic event!
Encrypt all of your digital goodies, enable multi-factor authentication, and treat every suspicious email like it’s a mix between a Tinder date gone wrong and a horror movie. Features like this are coming increasingly handy as threats scale up—hackers have been razor-sharp in their focus on credential stealing, trying to outsmart even the brightest tech heads in the business.
In this brave new world of information-stealing malware, understanding the landscape is half the battle. Once this information is pilfered, it’s then a hop, skip, and jump to breach corporate networks and create absolute chaos! I mean, who doesn’t want to slip into someone else’s bank account or ride the roller-coaster of a cyber heist?
So here’s a nutshell tip: Stay vigilant, my friends. The next time you see a shiny new AI image generator promising the best selfie of your life, remember it might just be a wolf in sheep’s digital clothing. And if you fancy avoiding a digital disaster, think twice before clicking on those links. Move smartly in the wild west of the internet, and who knows—you just might keep your hard-earned treasures safe!

Cybercriminals are leveraging deceptive AI image and video generators to spread harmful malware, specifically the Lumma Stealer and AMOS, targeting both Windows and macOS platforms. These malicious programs are designed to siphon off sensitive information, including personal login credentials and cryptocurrency wallet data from compromised devices.
This stolen data is meticulously compiled into an archive and transmitted back to the perpetrators, who may use the information for subsequent cyber attacks or trade it on illicit online marketplaces dedicated to cybercrime.
Fake AI image generators push Lumma Stealer
In a concerning trend over the past month, threat actors have established fraudulent websites masquerading as an AI video and image editing platform called EditPro. These sites have been observed promoting deceptive content through targeted advertisements on X, showcasing deepfake videos that portray public figures, including President Biden and former President Trump, in whimsical scenarios like enjoying ice cream together.

Source: BleepingComputer.com
Upon clicking on these appealing images, unsuspecting users are redirected to counterfeit versions of the EditProAI application. The website editproai[.]pro is specifically designed to propagate malware for Windows, while editproai[.]org targets macOS users. These sites have been crafted to appear legitimate, complete with professional layouts and typical cookie consent banners.

Source: BleepingComputer
However, selecting the “Get Now” buttons initiates the download of an executable file disguised as the genuine EditProAI application. For Windows users, the downloaded file appears as “Edit-ProAI-Setup-newest_release.exe”[[VirusTotal], while macOS individuals receive “EditProAi_v.4.36.dmg”[[VirusTotal].
Notably, the Windows malware has been signed using what appears to be a stolen code signing certificate from Softwareok.com, a recognized developer of freeware utilities, which adds a layer of credibility to the malware.
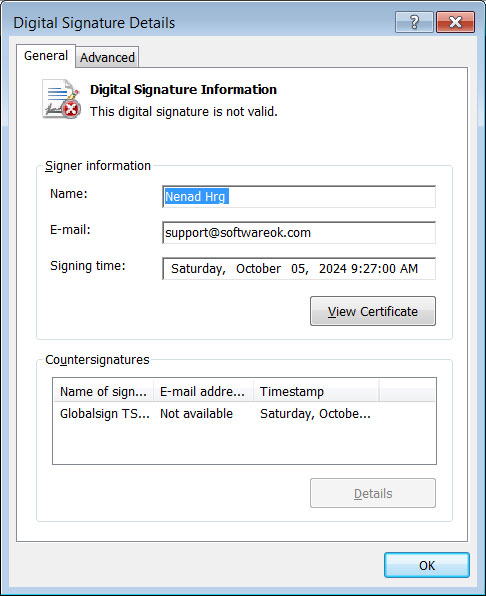
Source: BleepingComputer
Researcher G0njxa has indicated that the malware communicates via a control panel located at “proai[.]club/panelgood/”, allowing the attackers to retrieve the stolen data at a later time for their operations.
An AnyRun report has confirmed the execution of the Windows variant, identifying it as Lumma Stealer through its malware scanning capabilities.
If users have inadvertently downloaded these applications, it is crucial to treat all saved passwords, cryptocurrency wallets, and authentication mechanisms as compromised. Immediate action should be taken to reset these credentials, ensuring unique passwords are created for every site visited.
Moreover, it is highly advisable to enable multi-factor authentication on all critical accounts, especially for cryptocurrency exchanges, online banking services, email platforms, and financial management services, to bolster security.
The rise of information-stealing malware has been alarming over recent years, with threat actors increasingly engaged in widespread global operations aimed at pilfering users’ credentials and authentication tokens.
Recent campaigns pushing infostealers have exploited various tactics, including zero-day vulnerabilities, the deployment of fabricated fixes to GitHub issues, and even deceptive responses on StackOverflow to deliver payloads.
The captured credentials can subsequently be used to infiltrate corporate networks, facilitate data theft operations akin to the notable SnowFlake account breaches, and create disorder by manipulating network routing information.
What steps can I take to protect sensitive personal information from cybercriminals?
Ms, and any services containing sensitive personal information. This additional step makes it significantly more difficult for cybercriminals to gain unauthorized access, even if they have obtained your login credentials.
the landscape of cyber threats is constantly evolving, and it’s crucial to remain vigilant. Below are some proactive steps to enhance your security posture:
1. **Do Not Download Unverified Software**: Always download software from official sources. If something seems too good to be true, it probably is.
2. **Check for Signatures**: Before executing a downloaded file, check if it has been digitally signed and ensure it’s from a trusted source.
3. **Use Antivirus and Anti-Malware Tools**: Regularly scan your devices to detect and remove any malware.
4. **Regularly Update Software**: Keep your operating system and all applications up to date to protect against known vulnerabilities.
5. **Monitor Accounts**: Keep an eye on your bank and online service accounts for unauthorized transactions or changes.
6. **Educate Yourself and Others**: Stay informed about the latest scams, phishing attempts, and cybersecurity trends.
By following these guidelines, you’ll bolster your defenses against the ever-growing threats present in our digital lives. Stay safe out there!
