Recently we have seen how to create an L2TP/IPsec VPN tunnel on UDM. A few weeks ago Ubiquiti updated the UDM Pro SE to add WireGuard. So you can now use Wireguard as a VPN server from your Ubiquiti hardware and without having to tweak.
What is Wireguard?
WireGuard is an open-source VPN protocol that prioritizes security and simplicity. It was created in 2017 by Jason Donenfeld, a security researcher and developer, in response to existing VPN solutions which he considered slow and complicated.
One of WireGuard’s strengths is its use of modern cryptography. It uses the ChaCha20 symmetric cipher with Poly1305 for message authentication. This encryption is considered to be faster and more secure than traditional encryption algorithms.
WireGuard is also known for its use of public keys for user authentication. This means that users do not need to share a password to connect to the VPN network.
Here are some benefits of using Wireguard:
????Simplicity: Wireguard has a simple architecture and low code, which makes it easier to understand and maintain than other VPN protocols.
⚡Performance: Wireguard is designed to be fast and efficient, with low latency and low system resource usage.
????Security: Wireguard uses modern and secure encryption protocols to protect user data.
????Compliance: Wireguard complies with industry and regulatory standards, making it suitable for use in businesses and organizations that need to comply with certain security requirements.
We will therefore see in the rest of this article, how to configure Wireguard on a UDM Pro SE firewall from Ubiquiti.
Configuration WireGuard sur UDM Pro SE
To configure your Wireguard VPN server on your UDM Pro SE, from the settings, click on “Teleport & VPN” then click on “Create New” in the VPN Server section.
Here you will have the choice between two VPN protocols: Wireguard or L2TP.
In this case, we will select Wireguard.
Then give a name to your WireGuard VPN network, then in the “Server Address” section, make sure that the WAN IP address is displayed. Here, if you are in double NAT, then click on “Enter IP Address manually” to enter your WAN ip address. You can find your IP address via this site for example. Regarding the port, most often it is 51820 which is used, but you can completely change it, as a reminder it is a UDP port.
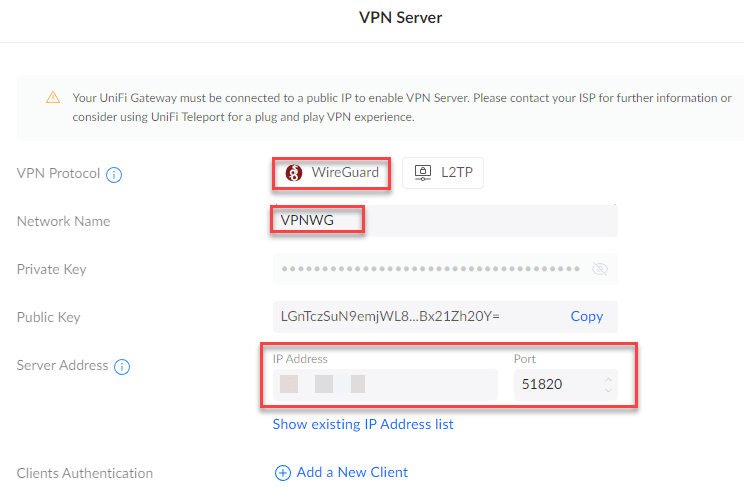
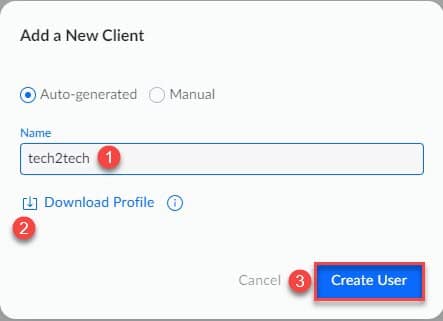
You can then click on ” Add a New client to add a user. Add the name of your user, then click on “Download Profile”, to finish click on “Create User”.
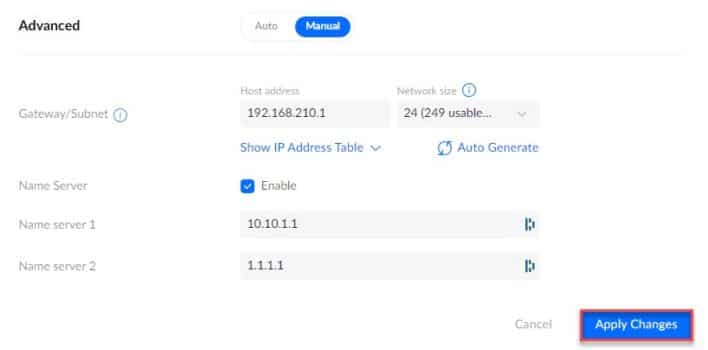
If necessary, you can now fine-tune your VPN configuration by selecting ” Manual in the advanced options. This will allow you to change the subnet of your VPN, but also to add the DNS servers you want. Complete the configuration by clicking on ” Apply Changes« .
Your VPN server is now configured. Keep the previously downloaded profile warm. It is this file that will allow you to connect with the client.
Installation et configuration du client WireGuard
Here we are ! We will now install the WireGuard client. This is one of the differences with a classic VPN such as L2TP which is already included in Windows, macOS or even on your smartphone. Here we will need to install the WireGuard application.
Download WireGuard
I will not explain here how to install the client since it is not rocket science. Once the client is installed, it is necessary to import your profile previously downloaded from the Network application of your UDM Pro SE.
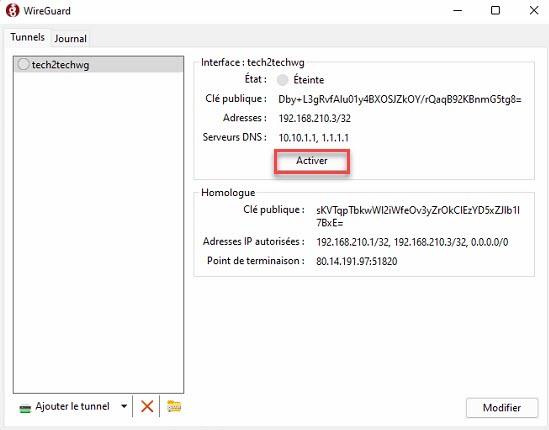
Click Activate to start the VPN connection.
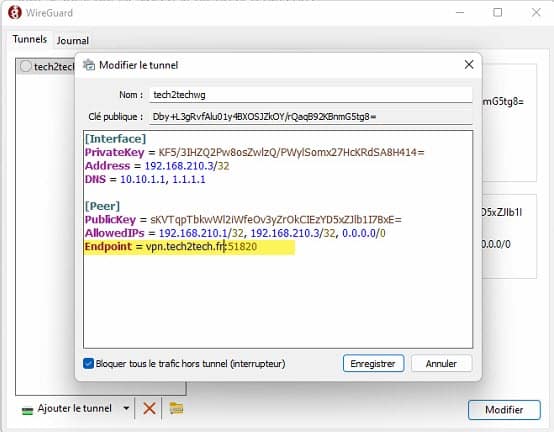
You can edit the Endpoint if you have a dynamic ip address via a dynDNS for example.
Adapt your firewall accordingly
Be careful, by default, your new VPN network will have access to your entire network. If for specific needs you only need access to a few devices or VLANs, then configure your firewall accordingly.
In my case, I add a blocking of this new network on all of my VLANs, however, I then authorize it to connect to a few IPs such as my home assistant, NAS server, ect…
For this I will create a first firewall rule to block all clients of my VPN from accessing all of my VLANs, here we will use the RFC1918 networks that I have already presented in a previous article.



