A zero-day remote code execution (RCE) vulnerability was discovered in the Spring framework shortly following a Chinese security researcher briefly disclosed a proof of concept (PoC) exploit on GitHub before deleting their account.
According to cybersecurity firm Praetorian, the unpatched flaw affects Spring Core on Java Development Kit (JDK) versions 9 and later and is a workaround for another vulnerability tracked as CVE-2010-1622allowing an unauthenticated attacker to execute arbitrary code on the target system.
Spring is a software framework to create Java applications, including web applications on the Java EE (Enterprise Edition) platform.
“In some configurations, exploiting this issue is straightforward, as an attacker only needs to send a specially crafted HTTP request to a vulnerable system,” said researchers Anthony Weems and Dallas Kaman. noted. “However, exploiting different configurations will require the attacker to do additional research to find payloads that will be effective.”
Additional details of the fault, dubbed “SpringShell” and “Spring4Shell“, have been withheld to prevent exploit attempts and until a fix is implemented by those responsible for the framework, Spring.io, a VMware subsidiary. It has also not yet received a Common Vulnerabilities and Exposures (CVE) identifier.
It should be noted that the flaw targeted by the zero-day exploit is different from the two previous vulnerabilities disclosed as part of the application this week, including the Spring Framework Expression DoS vulnerability (CVE-2022-22950) and the Spring Cloud Expression Resource Access Vulnerability (CVE-2022-22963).
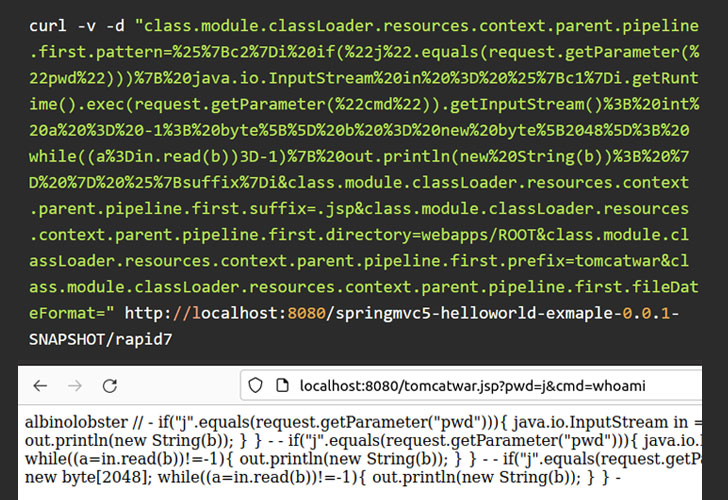
In the meantime, Praetorian researchers recommend “creating a ControllerAdvice component (which is a Spring component shared between controllers) and adding unsafe models to the deny list.”
Initial analysis of the new code execution flaw in Spring Core suggests that its impact may not be severe. “[C]Current information suggests that to exploit the vulnerability, attackers will need to locate and identify instances of web applications that are actually using DeserializationUtils, which developers already know to be dangerous,” Flashpoint noted in an independent analysis.
Despite the public availability of PoC exploits, “it is currently unclear which real-world applications are using the vulnerable functionality”, Rapid7 Explain. “JRE configuration and version can also be important factors in exploitability and likelihood of widespread exploitation.”
The Retail and Hospitality Information Sharing and Analysis Center (ISAC) issued a statement that it investigated and confirmed the “validity” of the PoC for the RCE flaw, adding that it was “continuing testing to confirm the validity of the PoC.”
“The Spring4Shell in-the-wild exploit appears to work once morest spring.io’s ‘Handling Form Submission’ stock sample code,” CERT/CC vulnerability analyst Will Dormann noted in a tweet. “If the sample code is vulnerable, then I suspect that there are indeed real-world applications that are vulnerable to RCE.”




:quality(80)/cdn-kiosk-api.telegraaf.nl/519964a0-c2e3-11ef-9519-06d92d542aed.jpg)
